You’re likely aware that any online activity comes with some level of risk. If you have a website, you’re not only responsible for your own information, but that of your users and customers as well. You may be hesitant to use WordPress if you have concerns about how secure it is.
The good news is that being aware of WordPress vulnerabilities can go a long way toward keeping your website safe. By staying proactive and following best practices, you should be able to ensure the security of your website and its users.
In this article, we’ll provide some general information about WordPress vulnerabilities. Then, we’ll have a look at five of the platform’s most common weak points and how you can fortify them. Let’s get started!
An Introduction to WordPress Vulnerabilities
While it’s not a pleasant thing to think about, cybercrime is increasing, and should be on every website owner’s mind. If you use WordPress as your Content Management System (CMS), you may have heard that it’s not an exceptionally secure platform.
These concerns primarily stem from the fact that it’s a hugely popular CMS, powering about 41 percent of all websites. This makes it a natural target for hackers.
One tactic attackers often use is injecting malware or adding spammy links to your website. While the occurrence of malware attacks overall decreased in 2020, the number of malware variants increased, so it is still a danger. If your site is compromised in this way, Google may blacklist it.
If the possibility of losing your hard-won rankings on Search Engine Results Pages (SERPs) isn’t enough, your information as well as that of your customers may become compromised. This could lead to you facing legal action and sustaining a blow to your professional reputation.
Are WordPress Websites Really That Vulnerable? (5 Weaknesses to Be Aware Of)
Now that we’ve discussed some of the consequences of a vulnerable WordPress site, let’s look at a few commonly exploited weaknesses. We’ve also covered some solutions to help you protect your site from them.
1. Outdated WordPress Core
When security issues are found in WordPress core, a dedicated team moves to address them quickly. News of these vulnerabilities travels fast among cybercriminals. Therefore, outdated core files are an inviting target for hackers who can take advantage of known exploits.
When a new version of WordPress is released, you’ll see a message in your admin dashboard. If you don’t see the prompt, you can simply navigate to Dashboard > Updates:
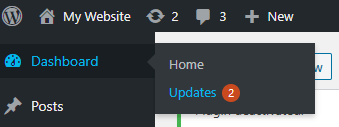
On this screen, you can configure your site to update automatically whenever a new version of WordPress core is released. If you prefer to perform these updates yourself, you can choose to implement automatic updates for only maintenance and security releases:
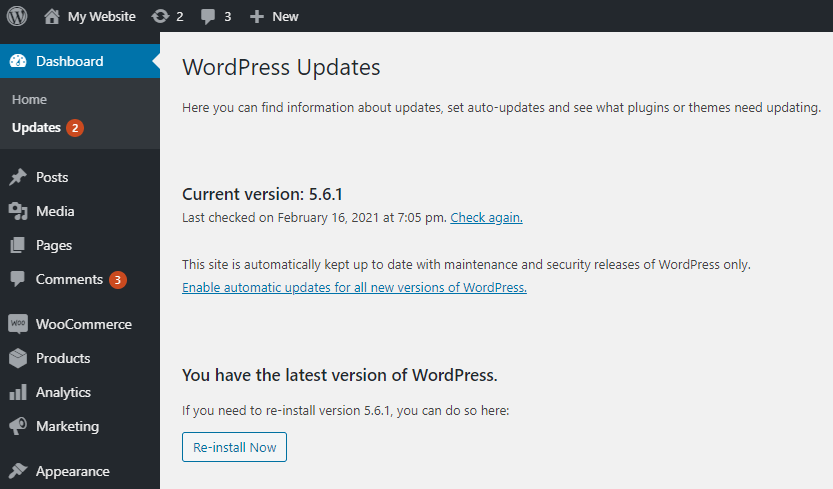
Alternatively, a vulnerability scanner should turn up an outdated version of WordPress as well as other potential issues on your site.
2. Outdated Plugins or Themes
Overall, WordPress is quite secure, thanks in part to its large, active community. However, many security breaches are due to themes or plugins that third-party developers have created. Much like the WordPress core team, these developers act quickly when vulnerabilities are discovered in their tools.
You can monitor the status of your themes and plugins from the same screen you used to check for WordPress core updates. Navigate to Dashboard > Updates and scroll down to see sections for themes and plugins:
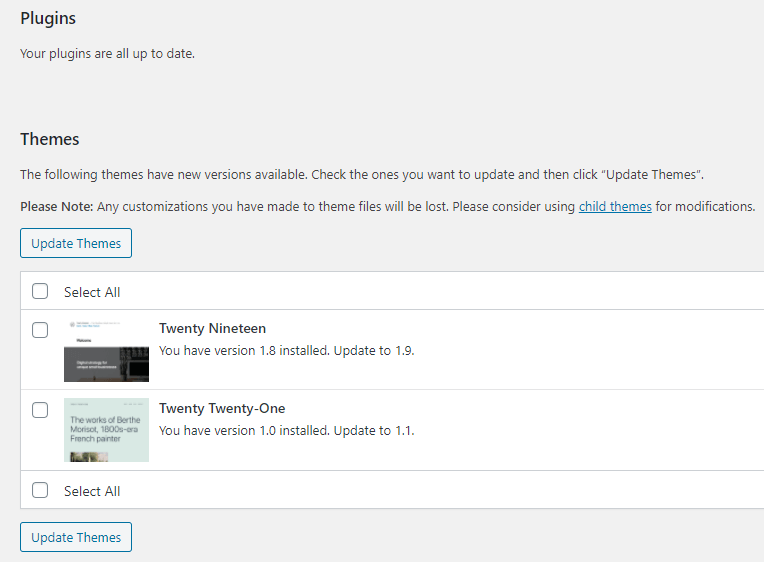
You may want to enable automatic updates for your plugins. You can do so by clicking on Plugins in the menu on the left side of your dashboard. From here, click on the Enable auto-updates link next to any plugin you would like to update automatically:
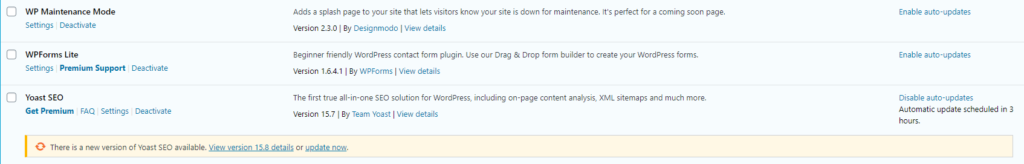
If you’d prefer a proactive reminder of these updates, WPSec can send you a push notification when it detects an outdated or untrustworthy plugin or theme.
3. Weak Admin Passwords
By default, the admin login page for all WordPress sites is set to yourwebsite.com/wp-admin. This page is a prime target for brute force attacks:
In a brute force attack, a hacker (or bot) will rapidly try large numbers of possible passwords in an attempt to gain access to your dashboard. Weak passwords are often cracked in a matter of seconds (with hashcat).
Even if the effort is unsuccessful, you may have your hosting plan suspended due to the load on your server. To keep your site as secure as possible, it’s critical to employ password best practices, such as:
- Create long passwords that are hard to guess but that you can remember.
- Use different passwords for each account.
- Never share your login credentials with others.
- Use a combination of upper and lower case letters as well as numbers and special characters.
Another tactic is to limit login attempts. While you should still strive for strong passwords, this can provide another layer of protection. You might also consider enabling Two-Factor Authentication (2FA) or changing the URL of your login page.
4. Nulled Themes or Plugins
Nulled themes and plugins are free versions of premium tools distributed by someone other than the developer. You can often find nulled versions of trendy themes:
These tools may include backdoors that attackers can use to access your site. You also won’t receive updates from the developers. This will cause your themes and plugins to become outdated quickly, and even more vulnerable to attack.
It’s always best to purchase the official licenses for the components of your website. Compared to the risk of having your site hacked, it’s a very worthwhile investment.
5. Poor User Role Practices
WordPress utilizes user roles in defining permissions for those with access to your website. These roles range from Subscriber to Administrator. Some plugins, such as e-commerce solutions, may create additional roles.
You can view a list of your site’s users and their roles by navigating to Users > All Users:
It may seem more straightforward to grant everyone working on your website admin privileges, but this can leave it open to attack. Those with admin permissions have a lot of power over your website and could take advantage of this fact. Additionally, it’s more challenging to spot an unexpected admin if you have a lot of them.
To avoid these scenarios, it’s best to adhere to the Principle of Least Privilege (PoLP). This rule states that each user should be given the lowest level of permissions required to perform their assigned tasks.
Conclusion
Being aware of the ways your WordPress site may be vulnerable to attack is the first step in guarding it against potential disasters. Monitoring these areas and performing regular scans of your website can help you ensure that it stays safe.
Keep a close eye on the following, and you’ll likely have less to worry about when it comes to WordPress vulnerabilities:
- Outdated WordPress core: Make sure to install all security patches to prevent cyberattacks.
- Outdated plugins or themes: Access the latest versions of other site components from their developers to fix security issues.
- Weak admin passwords: Follow password best practices to protect against brute force attacks.
- Nulled themes or plugins: Always pay for third-party plugins to make sure they’re legitimate.
- Poor user role practices: Follow the Principle of Least Privilege so all your users have appropriate permissions.
Do you still have questions about WordPress vulnerabilities? Ask away in the comments section below or file a ticket on our support system.


Pingback: 5 WordPress Weaknesses - MountainWP
Pingback: 4 Essential WordPress Security Plugins to Protect Your Website - WPSec