When it comes to complex password cracking, hashcat is the tool which comes into role as it is the well-known password cracking tool freely available on the internet. The passwords can be any form or hashes like SHA, MD5, WHIRLPOOL etc. Hashes does not allow a user to decrypt data with a specific key as other encryption techniques allow a user to decrypt the passwords.
Hashcat uses certain techniques like dictionary, hybrid attack or rather it can be the brute-force technique as well. This article gives an example of usage of hashcat that how it can be used to crack complex passwords of WordPress. Hashcat in an inbuilt tool in Kali Linux which can be used for this purpose.
USAGE
If a user wants to look that what hashcat facilitates, by running hashcat –help as shown below:
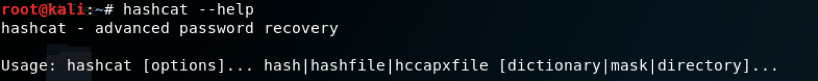
Some pictures are given below as example:
- [ Outfile Formats ] -
# | Format
===+========
1 | hash[:salt]
2 | plain
3 | hash[:salt]:plain
4 | hex_plain
5 | hash[:salt]:hex_plain
6 | plain:hex_plain
7 | hash[:salt]:plain:hex_plain
8 | crackpos
9 | hash[:salt]:crack_pos
10 | plain:crack_pos
11 | hash[:salt]:plain:crack_pos
12 | hex_plain:crack_pos
13 | hash[:salt]:hex_plain:crack_pos
14 | plain:hex_plain:crack_pos
15 | hash[:salt]:plain:hex_plain:crack_pos
- [ Rule Debugging Modes ] -
# | Format
===+========
1 | Finding-Rule
2 | Original-Word
3 | Original-Word:Finding-Rule
4 | Original-Word:Finding-Rule:Processed-Word
- [ Attack Modes ] -
# | Mode
===+======
0 | Straight
1 | Combination
3 | Brute-force
6 | Hybrid Wordlist + Mask
7 | Hybrid Mask + Wordlist
- [ Built-in Charsets ] -
? | Charset
===+=========
l | abcdefghijklmnopqrstuvwxyz
u | ABCDEFGHIJKLMNOPQRSTUVWXYZ
d | 0123456789
h | 0123456789abcdef
H | 0123456789ABCDEF
s | !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~
a | ?l?u?d?s
b | 0x00 - 0xff
- [ OpenCL Device Types ] -
# | Device Type
===+=============
1 | CPU
2 | GPU
3 | FPGA, DSP, Co-Processor
- [ Workload Profiles ] -
# | Performance | Runtime | Power Consumption | Desktop Impact
===+=============+=========+===================+=================
1 | Low | 2 ms | Low | Minimal
2 | Default | 12 ms | Economic | Noticeable
3 | High | 96 ms | High | Unresponsive
4 | Nightmare | 480 ms | Insane | Headless
- [ Basic Examples ] -
Attack- | Hash- |
Mode | Type | Example command
==================+=======+==================================================================
Wordlist | $P$ | hashcat -a 0 -m 400 example400.hash example.dict
Wordlist + Rules | MD5 | hashcat -a 0 -m 0 example0.hash example.dict -r rules/best64.rule
Brute-Force | MD5 | hashcat -a 3 -m 0 example0.hash ?a?a?a?a?a?a
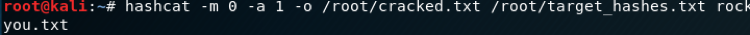
Combinator | MD5 | hashcat -a 1 -m 0 example0.hash example.dict example.dict1. Combinator
A combinator attack works by taking words from one or two wordlists and joining them together to try as a password. As shown below we took one wordlist and ran it against the hashes.
2. Wordlist
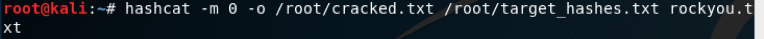
In this type of attack, we have selected the type of attack as 400 and 1 as the wordlist attack.

3. Rules based
This attack is one of the most complicated attack types.In Rule based attack,we selected the attack type as 0 and given the required input as wordlist and hash file.
Practical
We will take an example of a platform which has a wordpress login facility through which it allows to do further activities like manipulation of data in the database etc.
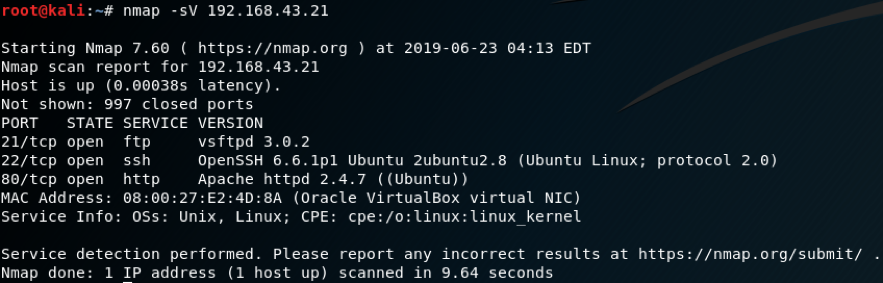
After running netdiscover command, ip was discovered and we got port 80 open. Now when we browse the ip along with the port we get a page, after which browsing on the links we come to know about that it was running WordPress on it.
Now we get some idea that if WordPress is running, our first task is to find WordPress login page. Fortunately, after running DirBuster we got a link where WordPress login option was there as shown below.

From here we can try some default inputs like qwerty, admin, qwerty123 etc. Luckily, after trying some defaults admin:admin matched and we got into the database comfortably.
Now there were many users who were having their password hashes stored and then it was the time to break these hashes.
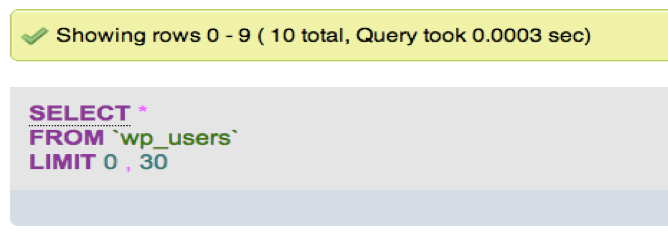
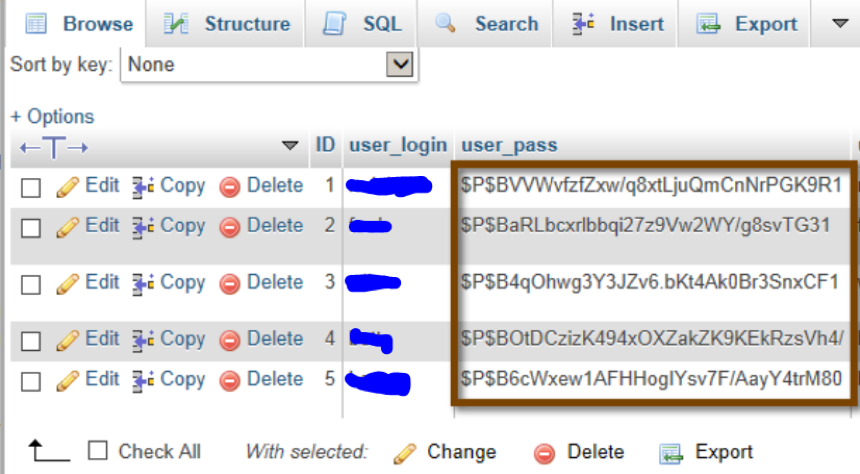
Here comes the use of hashcat by which as explained above we can crack the hashes to plain text. We will first store the hashes in a file and then we will do brute-force against a wordlist to get the clear text. As said above the WordPress stores the passwords in the form of MD5 with extra salt.
We will use the command shown below in which -m is for hash type, -a is for attack mode:

- -m 400 designates the type of hash we are cracking (phpass);
- -a 0 designates a dictionary attack;
- -o cracked.txt is the output file for the cracked passwords
The wordlist file rockyou.txt can be downloaded here: https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt
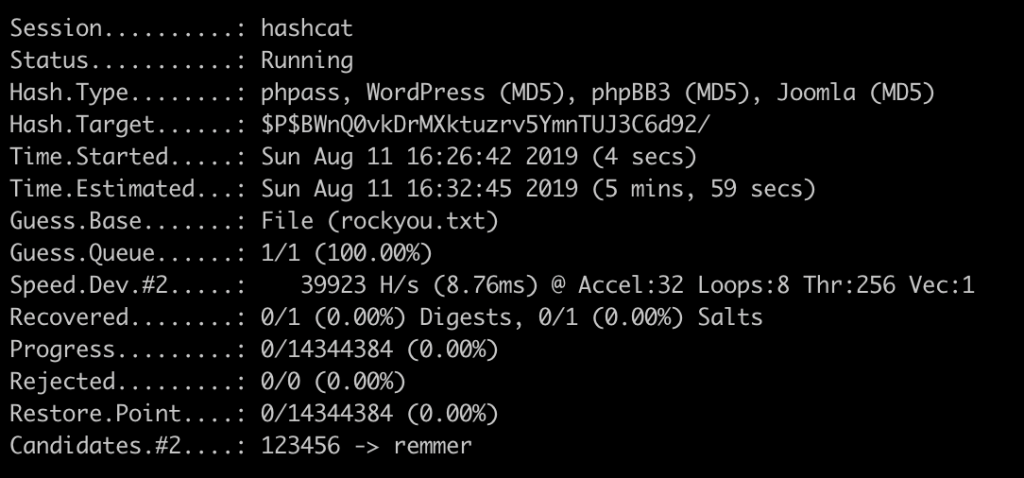
Now it started cracking the hashes and now we just have to wait until it cracks.
Successfully it was able to crack the hashes. As we found the list of user’s password were as shown below:
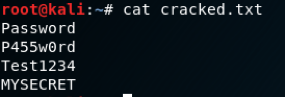
This was all about cracking the hashes with hashcat and this is how as shown above we can crack the hashes of WordPress as well.
WordPress uses by default the function wp_hash_password() which is (cost 8) 8192 rounds of MD5. The prefix in the hash is usually $P$ or $H$
If you would like to try to crack passwords yourself you can use the following hash:
$P$984478476IagS59wHZvyQMArzfx58u.


Can you please tell me that how can we save our wordpress site from this type of attack.
Just have a proper admin password 😉
This is not an attack in itself, it’s a how to use a tool AFTER you got access to the database.
> Now we get some idea that if WordPress is running, our first task is to find WordPress login page. ..
Well, to save you some time, the page is at /wp-admin/ and /wp-login.php basically everywhere, anybody remotely familiar with WordPress knows that.
Wrong.
Plenty of plugins out there that change the login slug from the default – and they’ve been around longer than your (rather arrogant) comment.
How i can brute wp login Page?
using hydra
Pingback: Hack Login Wordpress - login link
Pingback: Are WordPress Websites Really That Vulnerable? - WPSec