Author: Luke Stephens
Like any system, there are many ways to break into a WordPress installation, to name a few:
- Exploiting an out of date, vulnerable WordPress core
- Exploting vulnerable plugins or themes
- Man-in-the-middle attacks
- Social engineering
One of the most common ways to break into a WordPress installation is to simply find the password of one of the administrative users. Let’s walk through exactly how that might happen in a real-world scenario.
Setting the Scene
Jessica is a content marketing manager at Big Bank, part of her duties as the content marketing manager is to upload blogs to the website once per month, so naturally, she has an account on the WordPress installation at www.bigbank.com. Jessica also enjoys artisan chocolate, so she frequents artisanchocolate.com; the website of a small local chocolate maker who sells their goods online.
Unfortunately, her password for artisanchocolate.com is the same as her WordPress login for bigbank.com. Artisanchocolate.com has an SQL injection in their website which allows a hacker to download the user database, including passwords.
Once the attacker downloads the users and passwords for the ArtisanChocolate database, she gets to work searching the users on LinkedIn to see if any of them may be useful. Sure enough, she finds Jessica on LinkedIn, and notes that she is the content marketing manager for BigBank.
The attacker then navigates to bigbank.com/wp-admin, and tries to authenticate using Jessica’s credentials from artisanchocolate.com – it works! Now the attacker can change BigBank’s website, or upload a malicious plugin to gain remote code execution on the server, and potentially pivot into the bank’s internal network. 😬
For those of you who, like me, don’t have the patience to read the whole story, the flow goes something like this:
- Someone uses the same password for WordPress and another service
- Other service gets hacked
- Attacker uses password from other service to gain access to WordPress account
This story is fictional, but this situation occurs every day. The same flow is often used to break into cryptocurrency accounts or take control of high-profile social media accounts. There are even services online that allow attackers to search an email address and return all details that have ever been in a public data breach. Scary stuff!
What went wrong?
Of course – we should never use the same password for multiple services, but unfortunately people do. As a security person tasked with defending a company’s network, it is usually impossible to detect when one of your users is reusing passwords – so we need a different method of keeping users safe; that’s where multi-factor authentication (MFA) comes in.
What is Multi-Factor Authentication?
The goal of authentication is to identify who a user is. There are 3 ways to achieve this:
- Something you are: refers to checking biometric markers (fingerprints, iris scanners, voice recognition).
- Something you have: refers to checking if the user possesses something physical, for example, a device. A basic example of this would be possessing a key to open a lock.
- Something you know: for example, a password!
The more methods (factors) we use to identify the user, the more certain we can be that the person authenticating is who we think they are when they authenticate.
How to implement MFA in WordPress
There are plenty of WordPress plugins for implementing multi-factor authentication. The 5 most popular ones are:
Which one you use is entirely up to you, but for the purposes of this article, we’re going to use Two-Factor because it is:
- Simple
- Open-source
- Actively maintained
- Supports multiple providers including:
- Email codes
- Time Based One-Time Passwords (TOTP)
- FIDO Universal 2nd Factor (U2F)
- Backup codes
Installing the Two-Factor Plugin
The first thing we need to do is log in to your WordPress installation’s administrator dashboard. The login is typically located at /wp-login.php.
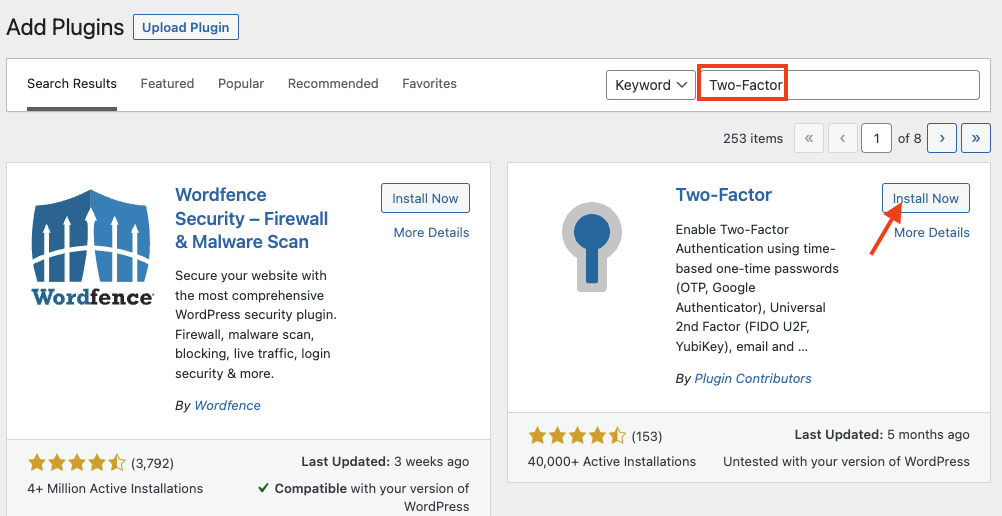
In the menu, click on Plugins > Add New, then search for “Two-Factor”. Locate the plugin called “Two-Factor” and click “Install Now”.
It will take 10-30 seconds to install – once the installation is complete, click “Activate”.
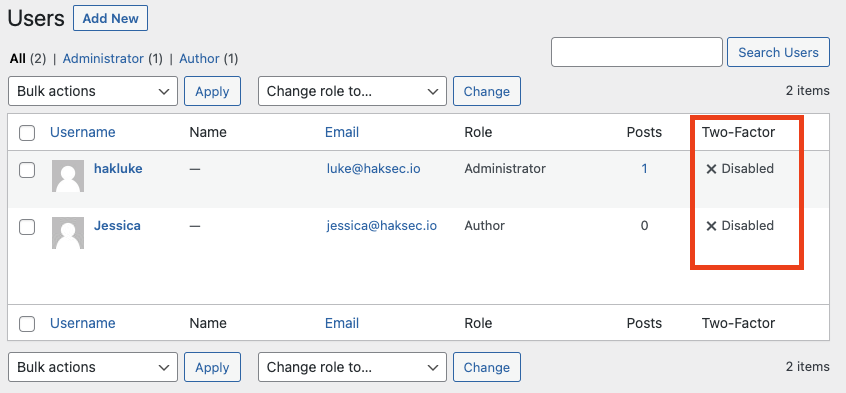
Once it has finished activating, head over to your “Users” tab from the menu. You will notice that there is now an additional column in the user list, called “Two-Factor”.
Let’s add two-factor authentication to Jessica’s account. Hover over the username that you wish to edit and click the “Edit” button. If you scroll down, you will notice that there is a section for Two-Factor options, as shown below:
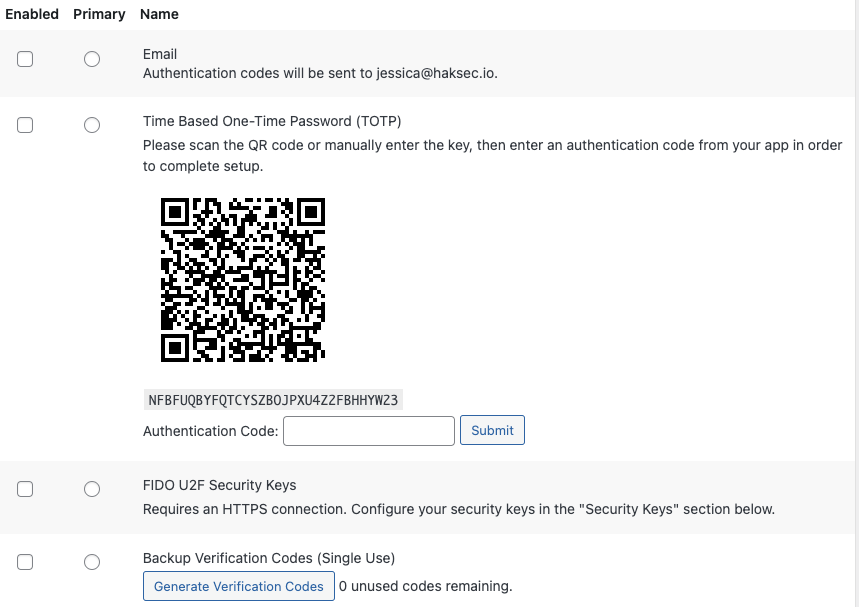
You can choose to set up whichever methods you wish, but in this example, we’re going to set up Google Authenticator using the QR code. Jessica could use any authenticator application on her phone, there are many available for both Android and iOS including:
- Google authenticator
- Duo
- Authy
- LastPass
- Auth0
- Many more!
But for the purposes of this article, we’ll use Google Authenticator. Jessica would download the Google Authenticator app on their phone, and be greeted with the following screen:
Jessica could enter the setup key if we provide it (the long string of random characters under the QR code in the screenshot above), but it is usually easier to scan the QR code using the phone’s camera, which is what we did in this case. As soon as the QR code is scanned, the account will be added to Google Authenticator, and start generating TOTP codes, like the one below:

We now need to enter the generated authentication code into WordPress and click “Submit”.
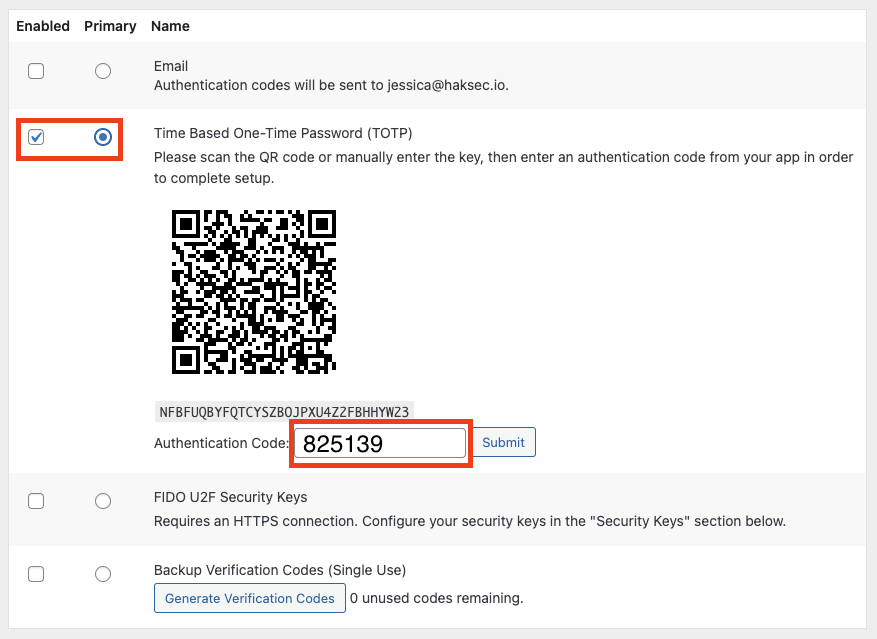
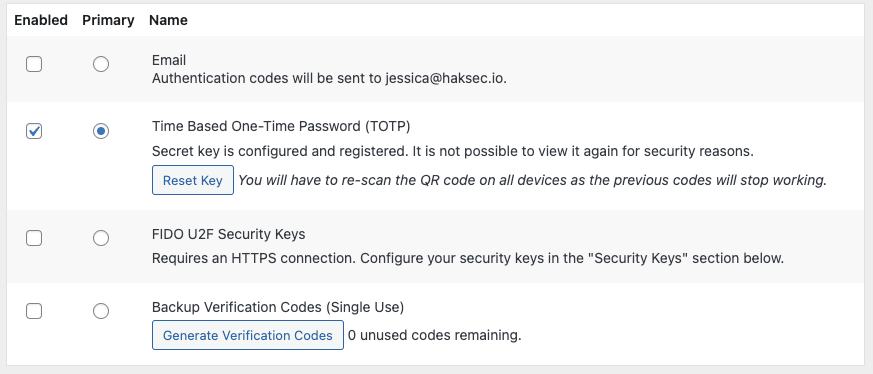
Ensure that “Enabled” and “Primary” are checked for the TOTP option in the screen below, and then click “Update User” at the bottom of the page.
Just to make sure it’s all working, let’s log out of WordPress, then log back in to /wp-login.php as Jessica.
Sure enough, we are greeted with a TOTP prompt:
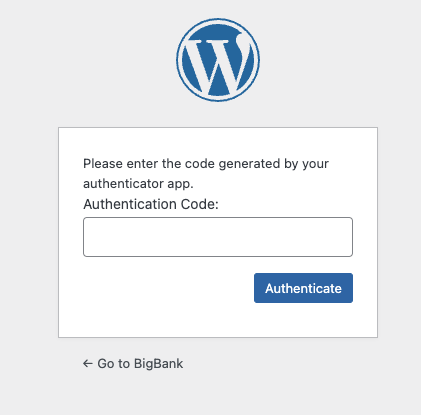
Entering the auth code from Jessica’s phone logs her in.
Conclusion
We have now implemented two-factor authentication by requiring something Jessica knows (her password) and also something she has (her phone, with the Google Authenticator app). We can rest easy knowing that if a malicious attacker came into possession of Jessica’s password, they still would not be able to log in to bigbank.com, and Jessica can continue buying her favorite artisan chocolates!

