Author: Devansh Bordia
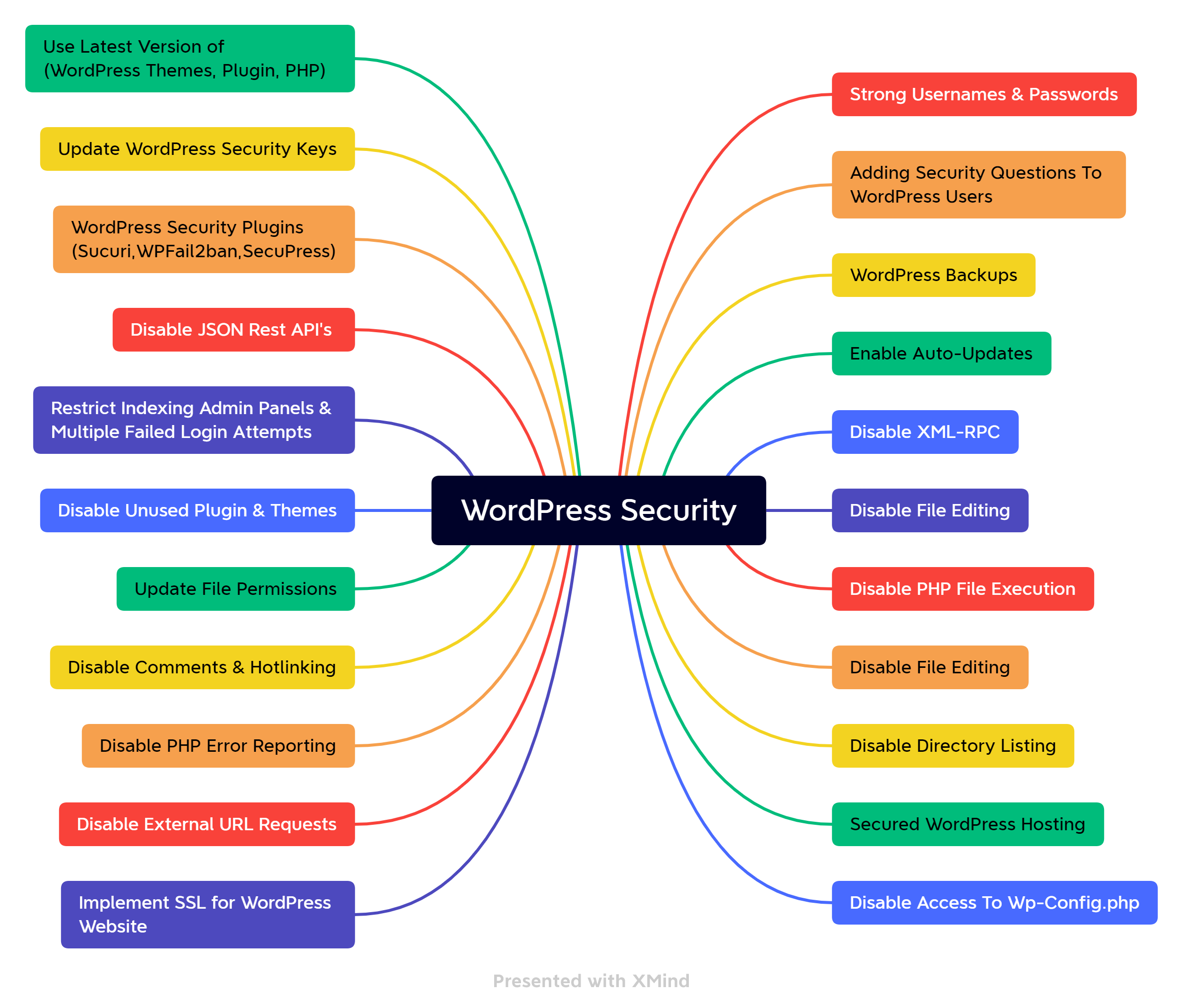
WordPress is the world’s most popular content management platform, used on 45% of websites. This also makes it an attractive target for malicious attackers! In 2021, more than 1.5 million WordPress websites were compromised. In this article, we will cover many ways that your WordPress instance may be attacked, and how to defend against them.
WordPress Vulnerabilities
In this section, we’ll cover the most common vulnerabilities in WordPress installations, including:
- Weak passwords
- Shared hosting
- Outdated software (WordPress Core, plugins, themes, PHP, web server)
- Lack of server hardening (change of security keys, preventing PHP execution, disabling file write access, hardening underlying infrastructure, etc.)
- Incorrect file permissions
Weak Passwords
The most common way to compromise a WordPress website is to exploit weak passwords. Attackers can bruteforce weak credentials to gain unauthorized access to the administrative dashboard.
Shared Hosting
Shared hosting is a popular choice for web hosting because it is cheaper. In shared hosting environments, multiple websites are hosted on a single server. The security pitfall occurs when an attacker who has access to the shared system exploits a privilege escalation vulnerability within the server, giving them underlying control of your website.
Outdated Software
Plugins and Themes
Plugins and themes can be installed in a WordPress installation to extend functionality. These plugins can be developed by anyone, and do not necessarily have the same security posture as WordPress Core. Plugins and themes can introduce vulnerabilities like Cross Site Scripting (XSS), Remote Code Execution (RCE), Open Redirects, SQL Injection (SQLI) etc. These vulnerabilities are typically fixed in more recent versions, so updating frequently is essential.
Server-Side Software
To run WordPress, you will need to install at least PHP, MySQL and a web server such as Apache. It is important to keep these components up to date, because a vulnerability on any of these could result in full compromise of the website.
Lack of Server Hardening
Server Hardening eliminates the potential entry points for attackers by disabling or removing access to specific files, accounts, ports, services, and applications. It may also include configuring the server in such a way that it reveals less information about itself, or is generally more resilient to attack. There are several features in WordPress such as file editor, hotlinks, PHP execution, and directory browsing which would introduce multiple vulnerabilities such as Remote Code Execution (RCE), sensitive information disclosure, Cross Site Scripting (XSS), and Denial of Service (DOS).
Incorrect File Permissions
File permissions are used to control access to files on the web server. The wp-content and wp-admin folders are used in WordPress to control the access to resources. By default, we should use 755 permissions for both of the folders because it restricts people from making any write changes within these folders.
Misconfigured file permission could allow the attacker to implant backdoors, modify settings, and gain unauthorized access to sensitive information.
Best Practices for WordPress Security
In this section, we will talk about some of the best practices that should be used while deploying a WordPress website.
Implement a Password Policy
Implementing a strong password policy is a security practice which should be implemented across all WordPress instances. The iThemes security plugin allows WordPress users to enforce a strong password policy and also checks if your password has been compromised using the HaveIBeenPwned API.
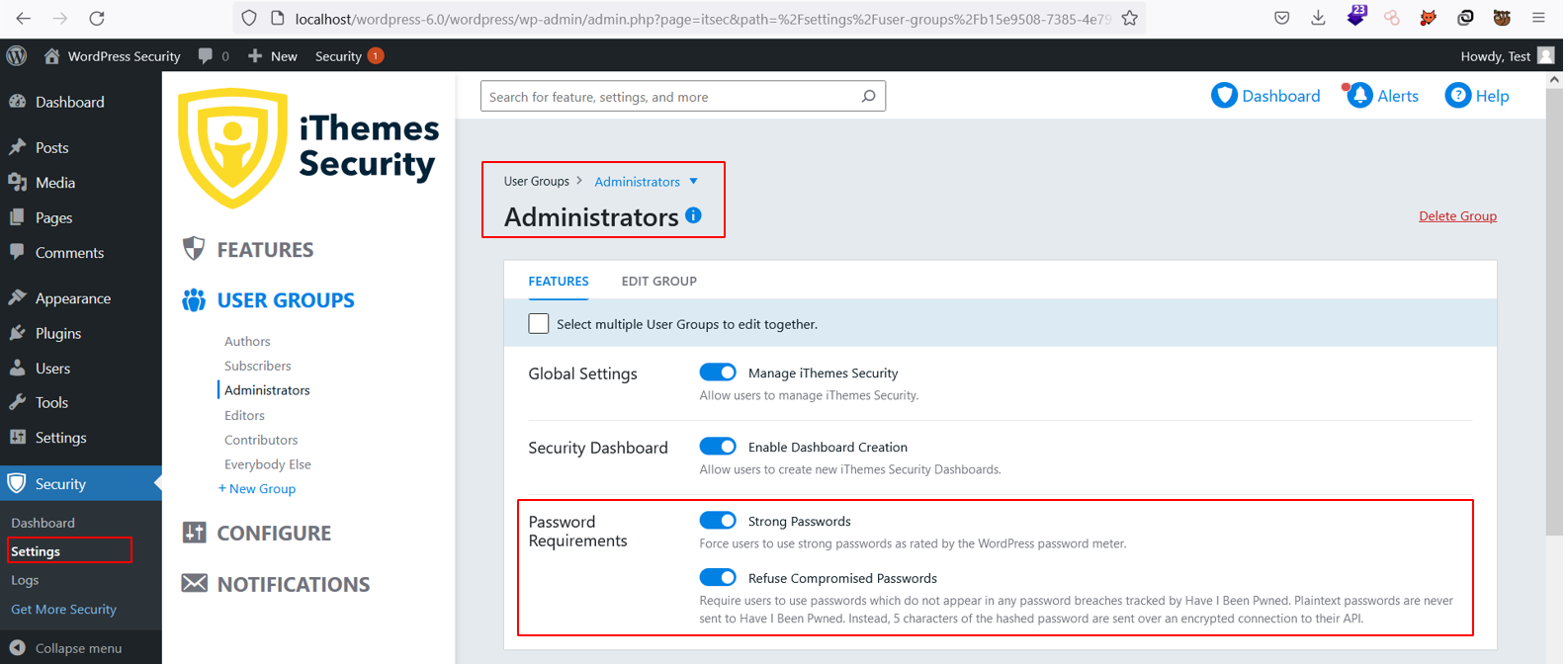
A strong password is at least 10 characters, consisting of numbers, symbols, uppercase and lowercase letters. Passwords should not be reused on any other service, and no part of the password should be a dictionary word, name, or any pattern that might be identifiable to you (e.g. your date of birth or pet’s name).
Changing Default Admin Username
In many WordPress instances, the administrator’s username is “admin”. Changing the “admin” username makes it more difficult for attackers to brute-force because they need to find both the username and the password, instead of just the password.
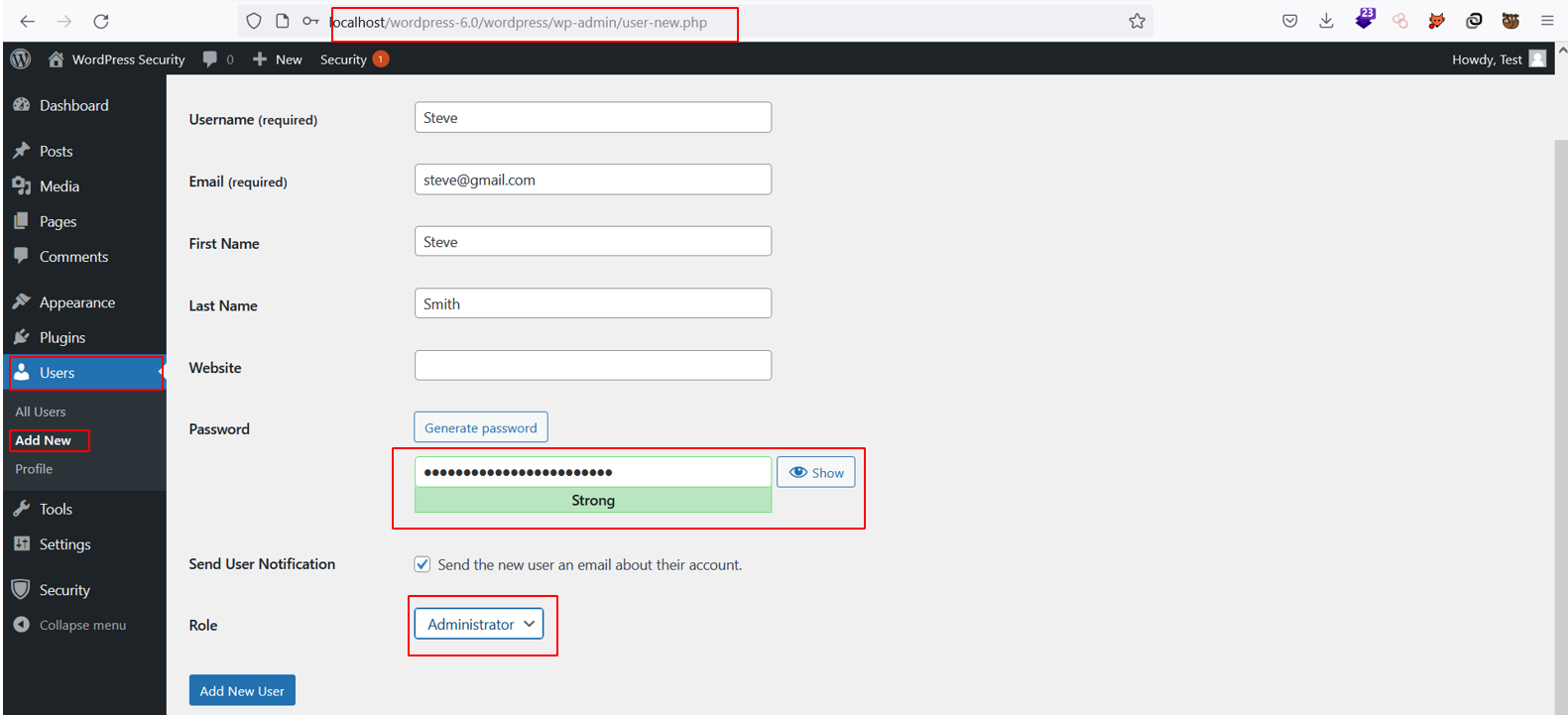
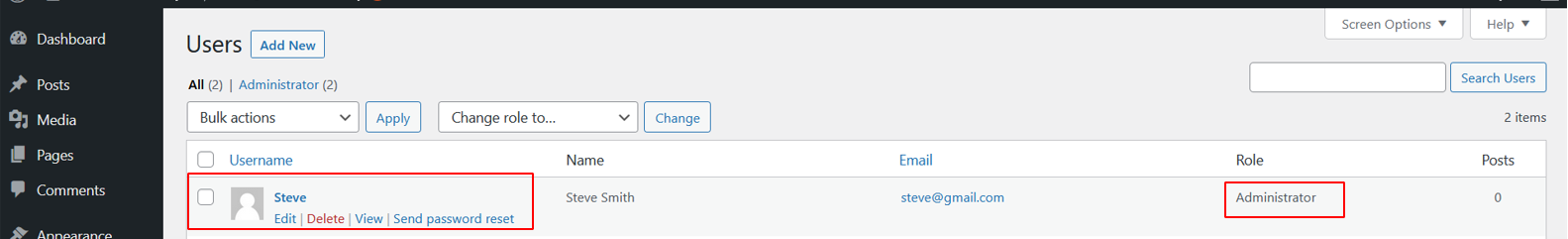
In the screenshots above we created a user “Steve” and deleted an old user.
Disable Pingbacks
Pingbacks are a feature that notify people when their content is being referenced in another blog. An attacker can leverage the pingback functionality to launch a Distributed Denial of Service (DDOS) attack. While this does not compromise your server directly, it does allow attackers to use your server to amplify their own attacks, which may affect the performance of your site.
To disable pingback we can use two methods:
- Using WordPress dashboard
- Using htaccess
Disabling Pingbacks Using WordPress Dashboard
Navigate To:
Settings → Discussion → Disable allows link notifications from other blogs (pingbacks & trackbacks)
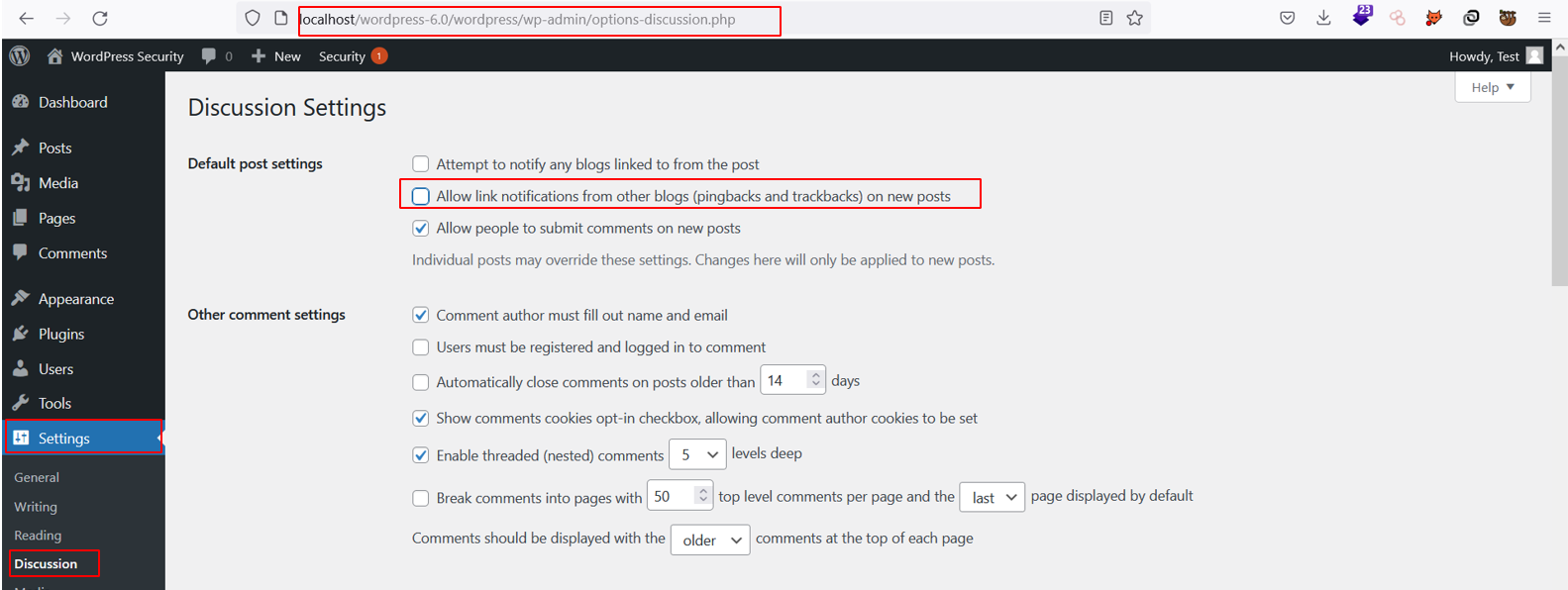
Disabling Pingbacks Using htaccess
We can completely disable pingbacks by modifying the code in the ‘.htaccess’ file which is used by our web server. To do so, we need to add the following code into the website root directory:
#XML RPC Interface Protection <FilesMatch "^(xmlrpc\.php|wp-trackback\.php)"> Order Deny,Allow Deny from all </FilesMatch>
Enable Auto-Updates
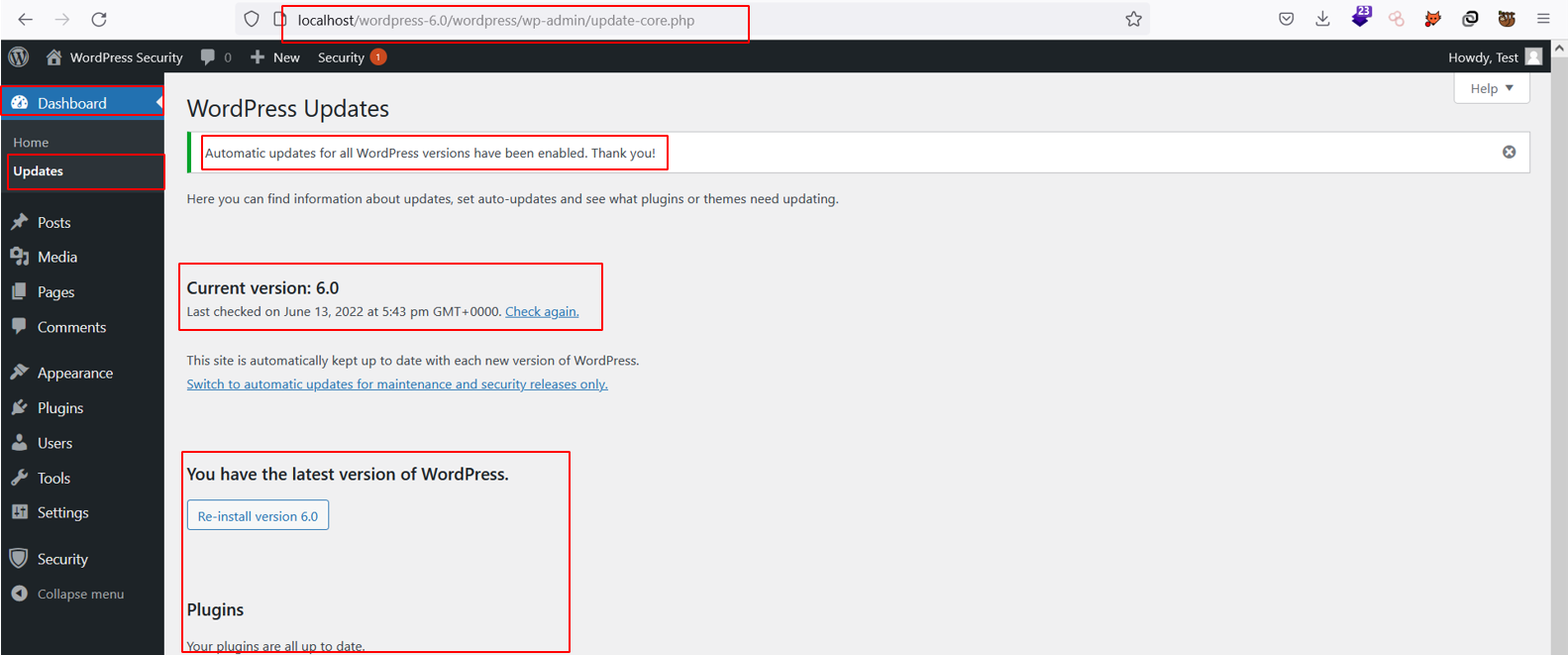
Auto-Updates is a feature that allows WordPress to automatically update plugins and themes when they become available, reducing the window of time that an outdated component may be exploited. We can enable auto-updates from the WordPress dashboard by navigating to:
Dashboard → Updates → Enable Auto-Updates
Disable PHP Editor
PHP editor is a feature that allows you to insert code within WordPress themes and plugins. If an attacker has access to the editor, they can insert arbitrary PHP code, leading to full compromise of your underlying web server, your entire WordPress instance, and your database. Reduce the likelihood of these types of attacks occurring by disabling PHP editor.
How to Modify wp-config.php To Restrict File Editing
Append the following code into the ‘wp-config.php’ file to restrict the edition of files within the WordPress administrative area:
// Disallow File Editing define( 'DISALLOW_FILE_EDIT', true );
Disable External URL Requests
There are instances where WordPress would need to make external requests to use plugins or themes. However, if left unfiltered these external requests can allow attackers to exfiltrate data and perform malicious operations on your website. To avoid these scenarios, we can add the following code to the ‘wp-config.php’ file
#Block External URL Requests
define('WP_HTTP_BLOCK_EXTERNAL', true);
#Whitelisted Domain
define('WP_ACCESSIBLE_HOSTS', 'test.com');
Disable Directory Browsing and JSON REST API
The directory structure in WordPress is mapped using an index page on the website. Attackers who can view the directory contents can understand the overall directory structure. If they gain access to the system they can use this information to navigate through sensitive endpoints which leads to leakage of the sensitive information. Use the following code in the ‘.htaccess’ file of the website root directory to restrict directory browsing for WordPress:
Options -Indexes
Additionally, WordPress allows developers to use the JSON REST API to communicate, and create plugins and themes for publishing content. The REST API allows an attacker to retrieve sensitive information from the WordPress website. For example,they could retrieve information by sending a GET request to certain endpoints, such as /wp-json, /wp-json/wp/v2/users/, /wp-json/th/v1/user_generation, /wp-admin/install.php, /wp-admin/readme.html etc.
The Disable Rest API plugin allows the developers to restrict and control access to endpoints publically for both authenticated and unauthenticated users.
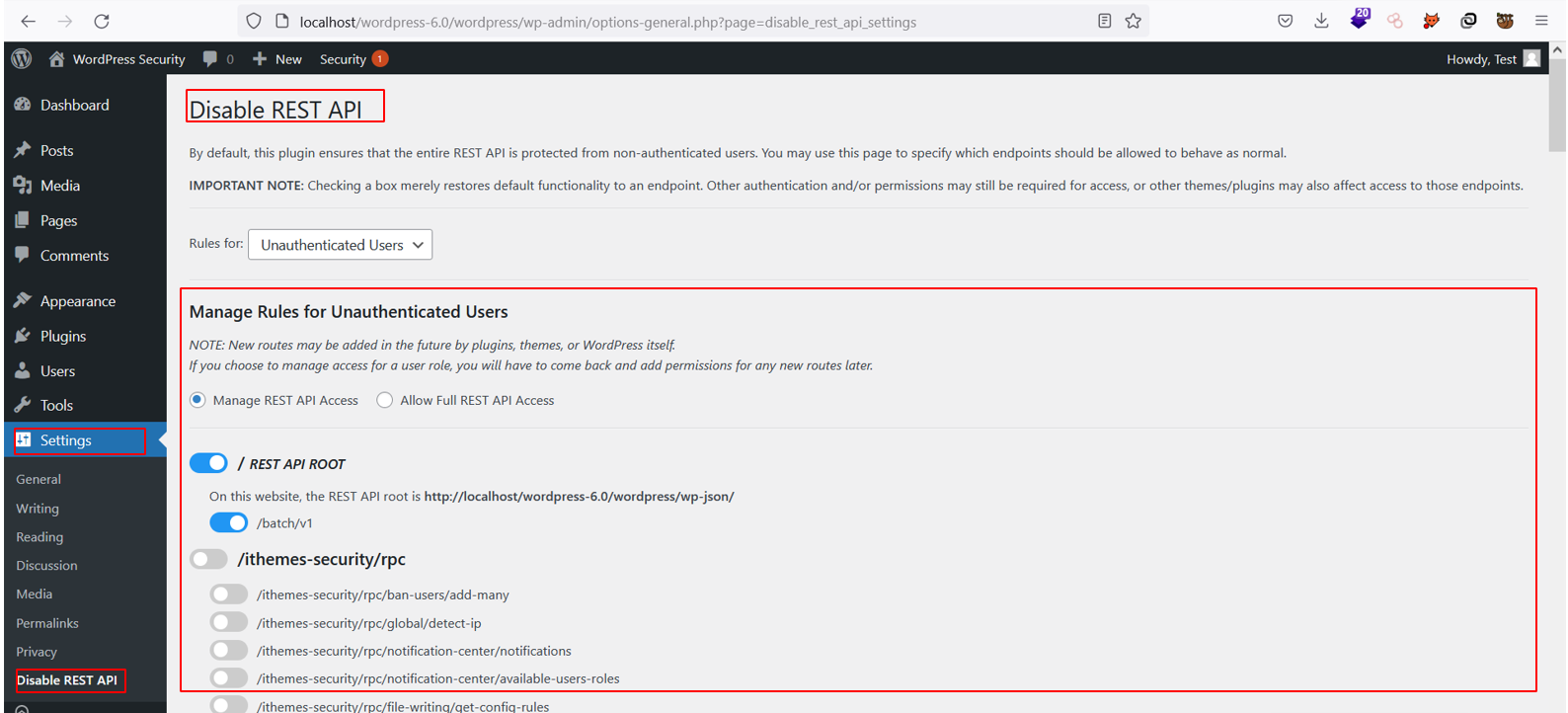
Disable Hotlinking
Hotlinks are used for referencing static resources like images, videos, and audio on someone else’s website by using a direct link. This consumes a lot of bandwidth and creates lag for users when viewing the website. For example, User A has a website with a lot of images and videos. If User B likes any of the images from the website of User A, they can add a direct link to the resource onto their website. The resource consumption on the server of User A will increase due to the surge of traffic from User B as the resources need to be loaded again. To avoid these resource consumption issues we can use the following to disable the hotlinking feature:
- All in one WordPress security and firewall plugin
- Apache
All in One WordPress Security and Firewall Plugin
The All in One WP Security & Firewall Plugin allows developers to disable the hotlinking feature. The plugin also allows the developers to customize different security parameters like firewall, user management, database & file security, etc.
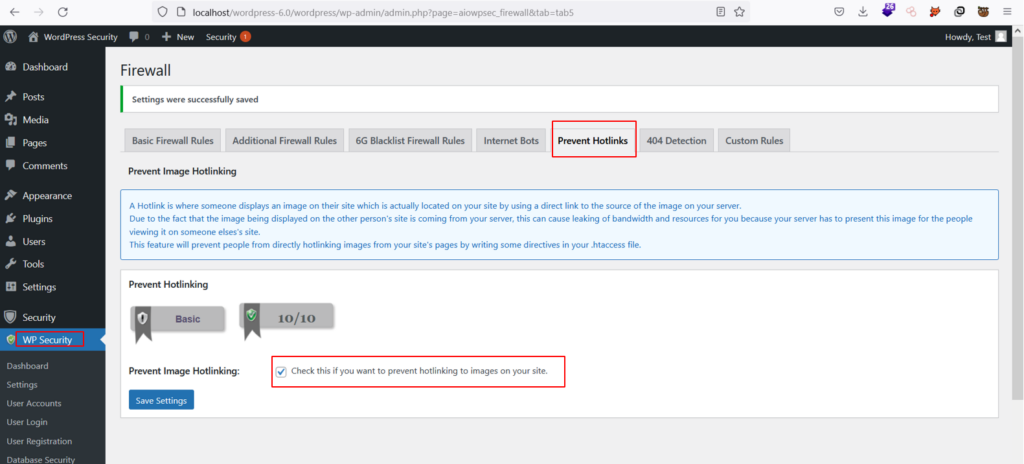
Apache
Within an Apache server, you can append the following code in the ‘.htaccess’ file within the root directory:
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?yourdomain.com [NC]
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?google.com [NC]
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?bing.com [NC]
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?yahoo.com [NC]
RewriteRule \.(jpg|jpeg|png|gif|svg)$ http://dropbox.com/hotlink-placeholder.jpg [NC,R,L]
Update WordPress Security Keys
WordPress security keys are a set of variables used for the encryption of cookies that provide additional security for your username & passwords, alternatively known as WordPress salts. These variables have their corresponding salts defined in the ‘wp-config.php’ file and they allow WordPress to encrypt your sensitive information within the browser for extra security.
To enable WordPress security keys, append the following code within the ‘wp-config.php’ file:
define('AUTH_KEY','w;:CxC{)OsRmMYqamrgQSZc gij~ZHH|&@ep&WPLbl>n<Z&`2`]0C+nfqQ5rFV,-');
define('SECURE_AUTH_KEY','gMJLW0U8#3b;=U$|,cz&l^>~cwvx;H3|+?z?9.V.(]sg{8ci6CV-5OSK#_i6>$n]');
define('LOGGED_IN_KEY','5w0e EX)[8=eO6G+~,$jXX%fhIv6Lt?3M4@M>- GEiC#(<&giV)@BydbR+JKv8vi');
define('NONCE_KEY','gJXENBe~4}==<Z|>kz#9d7uYaK2VdIi<1(,Cf;|=1JU&!}p@wp4(^pX+OxnM.Er');
define('AUTH_SALT','788-|F4Dc@B|-r$(`7.qy+K+X)HxMk)YtbiG&[+e/4~>]qe@dW,_V8B/-@#j Rr$');
define('SECURE_AUTH_SALT','N<PP!8|ABAlh^V)[A]-.54_r6u[Iaxv>8ioY|}V#7^^k8NtE7ugN+S~c mQtu(Y[');
define('LOGGED_IN_SALT','DOu}F2L-Ug9&mR=8=$;!q7}ph.|]~uNGFmqjpt.uVF^D^>q2H.(|Yn(E9Xx1@p)F');
define('NONCE_SALT','g[YC|f;F`EU;Gjvpc[y_%/+pOFh}_RWBF1*l=uV+c*&0;kR@$SD4-j{~L;me6aM');
Important: We recommend generating your own security keys. Do not use the above keys!
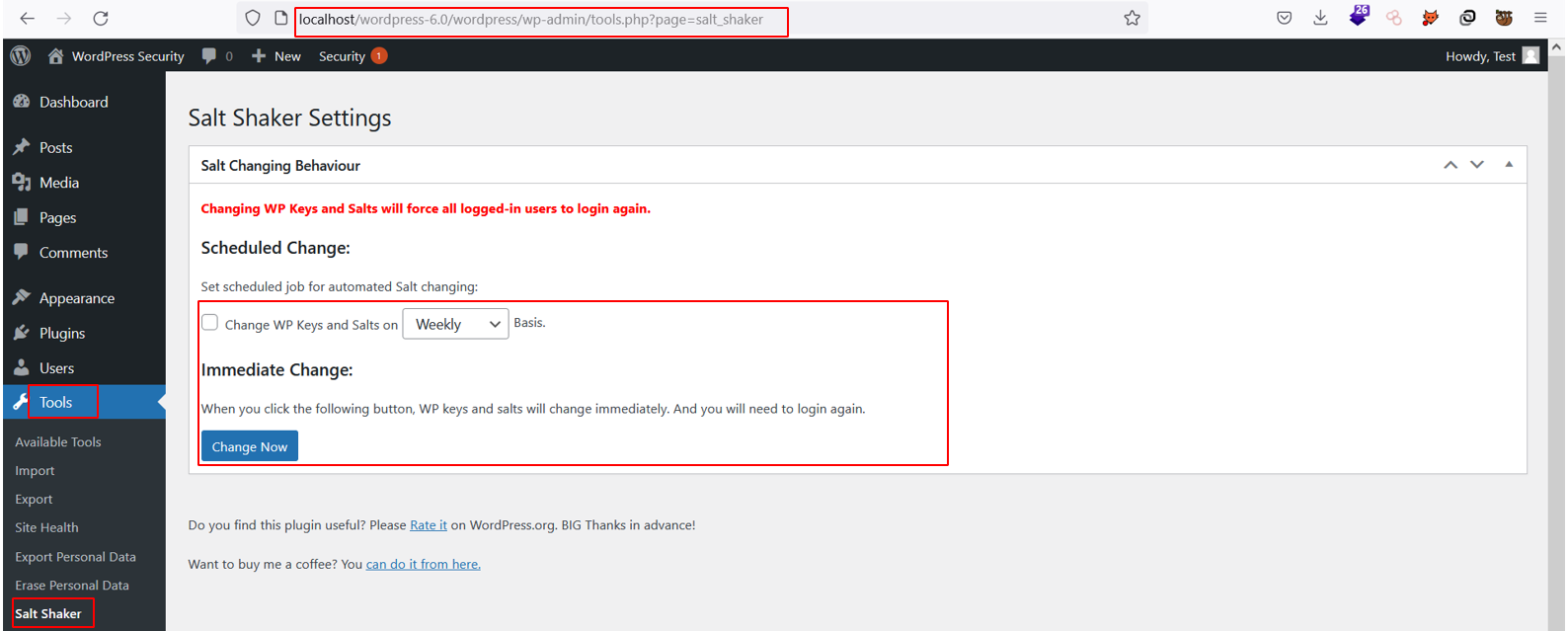
Salt Shaker WordPress Security Keys Plugin
Alternatively, you can use a WordPress plugin called Salt Shaker for generating and customizing security keys based on your requirements.
Navigate to: Tools → Salt Shaker → Change WP Keys & Salts
Other WordPress Security Plugins
Using different security plugins in WordPress allows the development team to have more precise control over security parameters of a WordPress application. Security plugins have several different features like:
- Password policy
- Multi-Factor Authentication (MFA)
- DDOS protection
- Preventing hot links & tracebacks
- Firewall & malware scanning
- Implementation of strong password policy
- Auto-updates & backups
- IP whitelisting & malware scanning
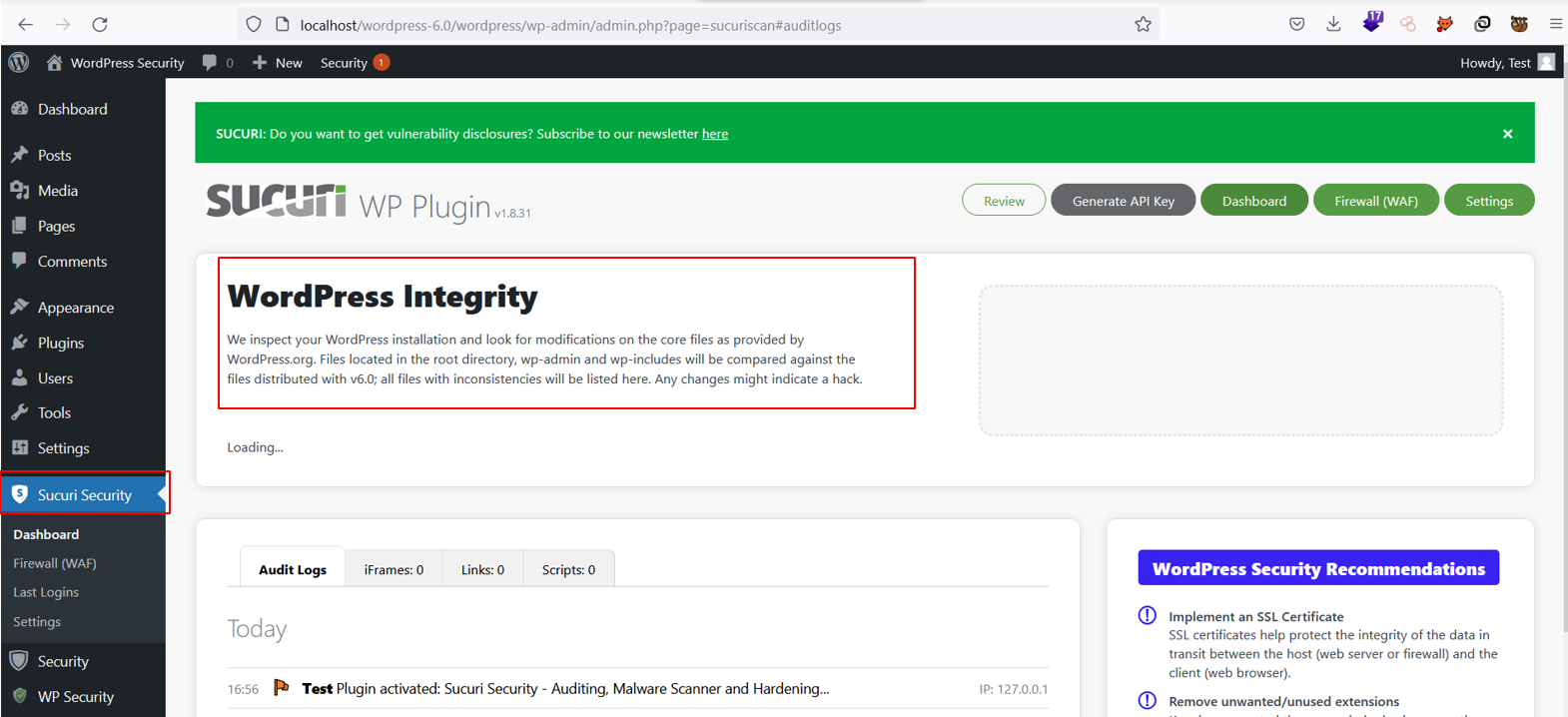
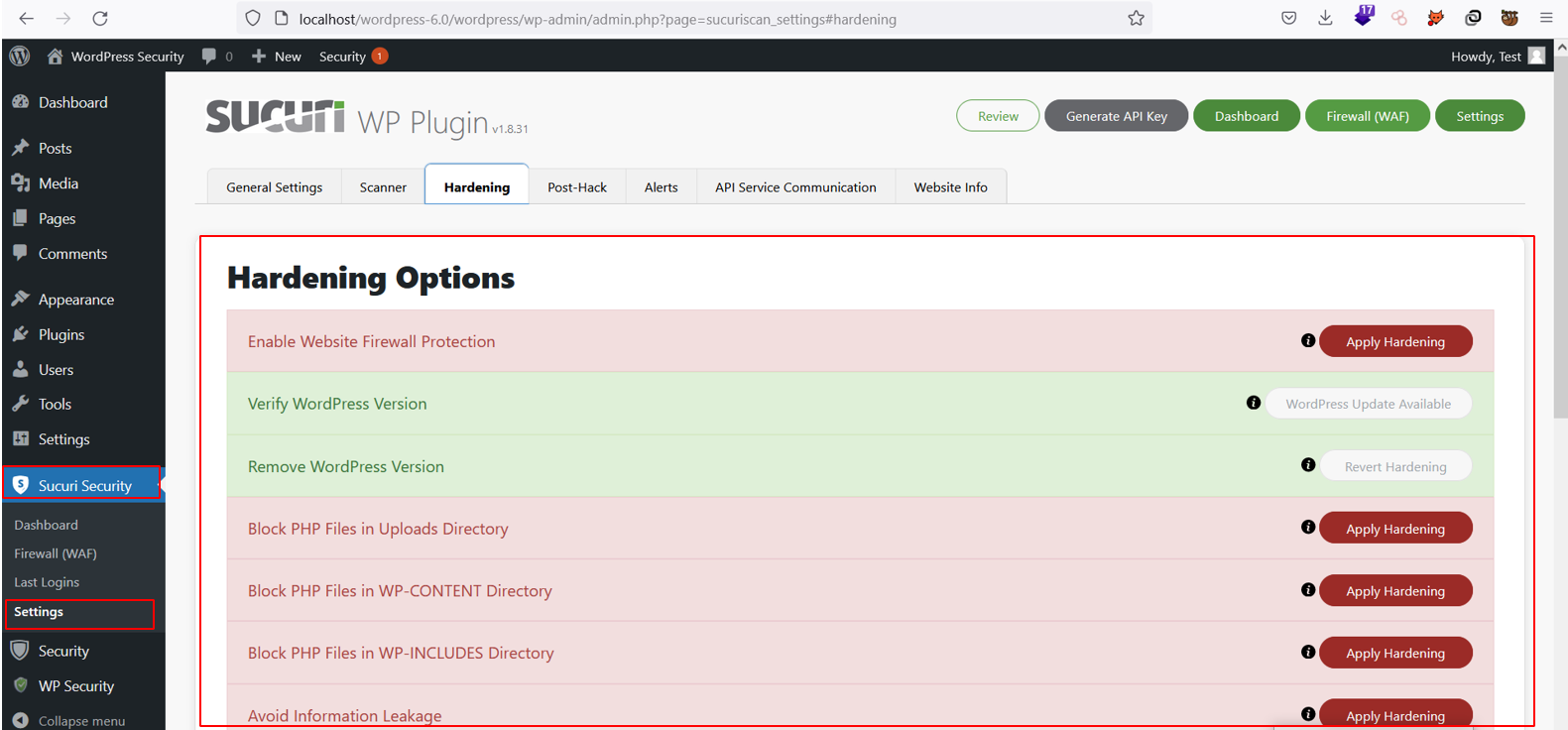
The most used security plugins in WordPress are Sucuri, iThemes Security, and SecuPress.
For example, the Sucuri plugin has many rich features that help you to enable firewall protection, remove visible WordPress versions, and block PHP files in the upload directory, amongst many others. This plugin allows you to implement several security hardening features into the WordPress website and reduces the chance of potential security vulnerabilities.
Implementing Multi-Factor Authentication
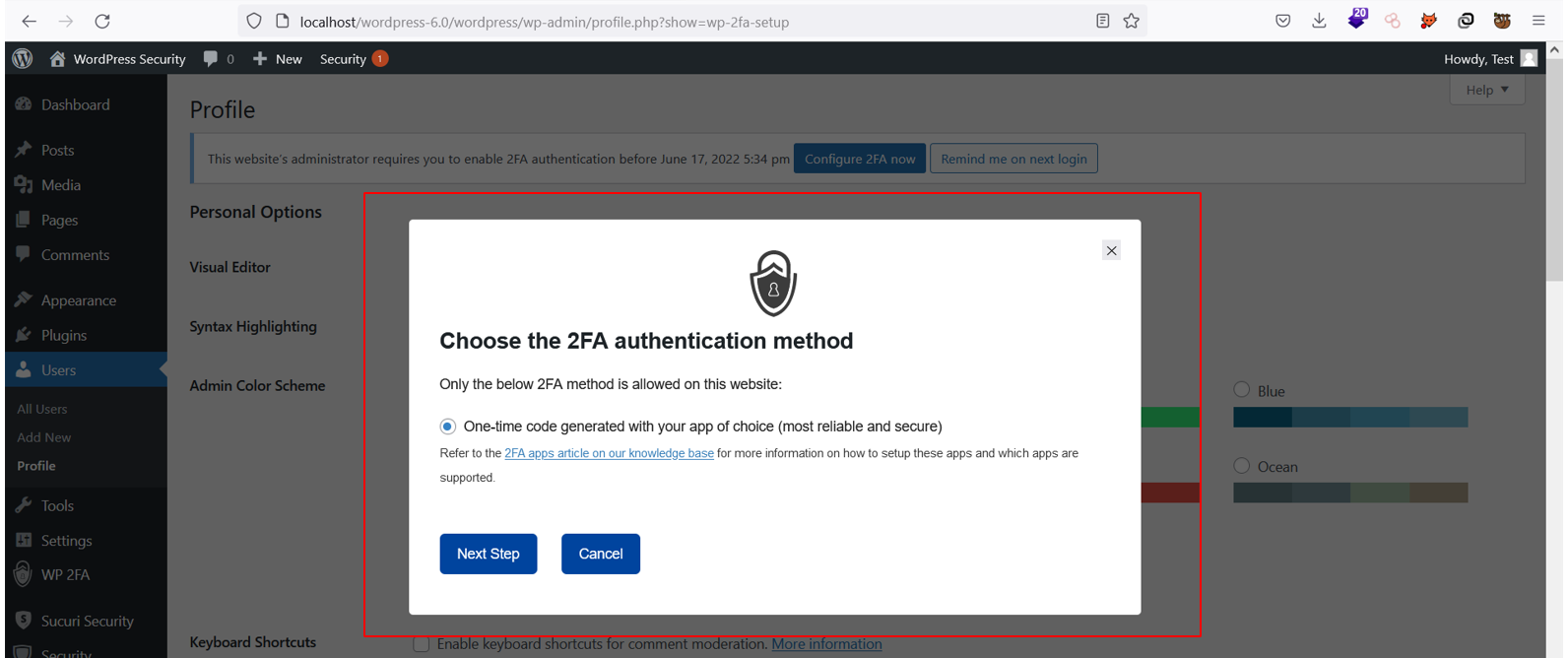
One crucial plugin you can install is WP-2FA which gives your WordPress site the added layer of security of Multi-Factor Authentication which is crucial when we are talking about the overall security posture of our websites. It uses Time-based One Time Password (TOTP), ensuring that users need to authenticate to the second layer of security. Below is an example of this plugin being set up and run:
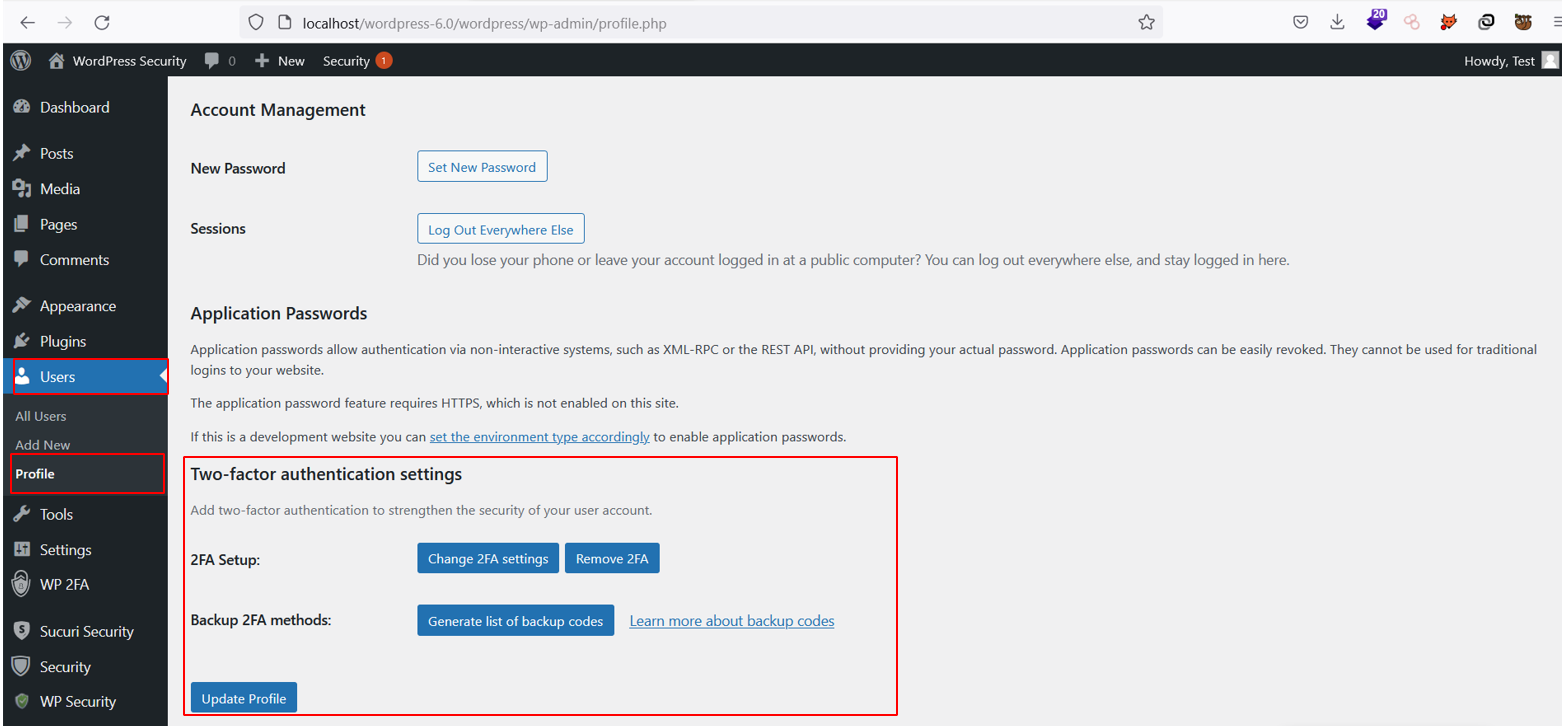
Conclusion
Now that we have walked through some of the common WordPress vulnerabilities and some best practices for combating them, you can confidently and securely deploy any WordPress application.


Thanks for the helpful article! You can also disable REST API with the Disable Everything plugin. I like that it is very light and simple so that is doesn’t slow your website down. It also comes bundled with lots of other optimization features that speeds up your site. Plugin is free and worth checking out: https://wordpress.org/plugins/disable-everything/
Pingback: 4 Essential WordPress Security Plugins to Protect Your Website - WPSec
Pingback: Best Practices for Maintaining WordPress Site Security - Betdico