When it comes to content management systems such as WordPress, hackers will often exploit file upload mechanisms to distribute malicious files which can be used to execute malicious code on a website, infect other websites, and allow hackers to gain full control over a server where your website is hosted.
In an effort to prevent exploiting file upload forms in content management systems, which are a popular way to build websites, a team of South Korean academics has developed FUSE, a new automated penetration testing tool.
Thanks to FUSE, they have discovered 30 vulnerabilities in various file upload mechanisms in 23 open-source web applications such as WordPress and other popular forum, store builder, and CMS platforms.
What Is FUSE?
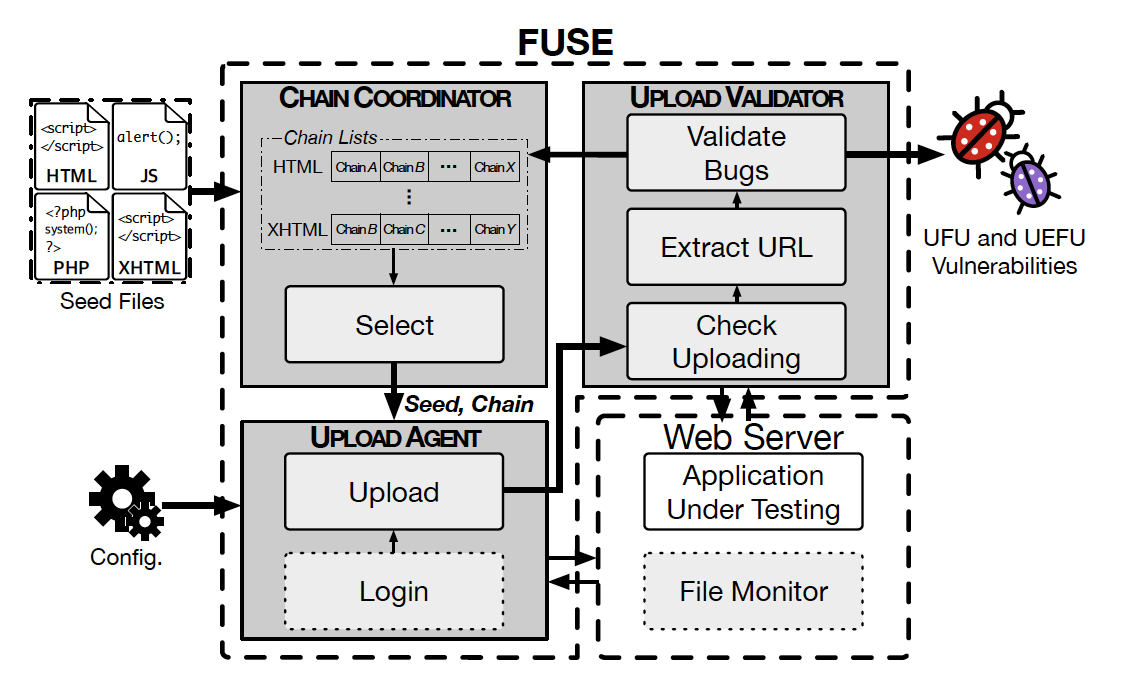
FUSE relies on automated penetration testing to discover vulnerabilities in PHP applications that are a direct result of unrestricted file uploads as well as unrestricted executable file uploads, commonly referred to as UFU and UEFU vulnerabilities.
It was developed by a team of academics from the Korea Advanced Institute of Science and Technology Constitution (KAIST) and the Electronics and Telecommunications Research Institute (ETRI).
FUSE consists of eight most common exploitation patterns and techniques that were identified during past file upload bugs. Along with the common patterns, FUSE also employs five new variations that were devised by the research team behind FUSE.
Putting FUSE To Use
Once FUSE was built, the research team decided to put it to use in 33 most popular web apps which included popular forum software, online store builders, and content management systems like WordPress.
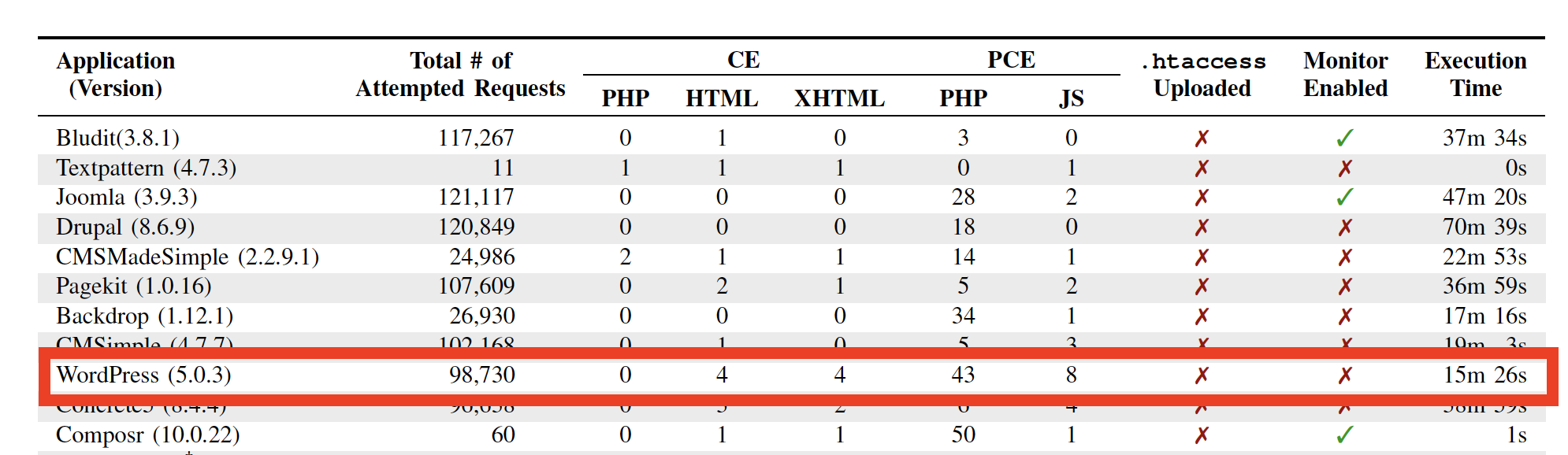
The tests took place in February of 2019 and the research team used a series of automated requests to exploit file upload mechanisms in these web apps. They attempted to plant malicious files and through these series of attempts, they uncovered 30 file upload bugs in 23 of the 33 applications they tested.
The researchers then reported the bugs and vulnerabilities to the corresponding vendors. While some vendors patched the bugs and vulnerabilities, others, like WordPress, have merely confirmed that they would address the vulnerabilities.
The research team provided an explanation for why some vendors didn’t patch the vulnerabilities stating that some of the bugs require admin access to be exploited which many vendors don’t consider a risk. This is because a hacker with admin access can hijack a server without relying on file upload exploits.
Unfortunately, while the research team behind FUSE did list which open-source applications contain bugs, they didn’t provide a list of applications that patched or didn’t patch the vulnerabilities. The reason is simple: they don’t want hackers to exploit this information and attack the applications that haven’t patched the vulnerability yet.
You can find out more about FUSE, the testing methodology behind it, and full results of the testing in white paper that’s available for download here.
Sign up for WPSec to do a free WordPress vulnerability scan.
WordPress photo by Shahadat Rahman on Unsplash

