A high-severity Cross-Site Scripting (XSS) vulnerability, tracked as CVE-2020-9334, exists in a popular WordPress plugin called Envira Photo Gallery, rendering over 100,000 websites vulnerable to phishing attacks, stealing administrator’s session tokens, etc.
In this Blog-post, we will cover what caused the flaw, an example Proof-Of-Concept showing exploitation in a sandbox environment, and mitigation steps.
What is the Envira Photo Gallery Plugin ?
According to the official documentation of the plugin,
We believe that you shouldn’t have to hire a developer to create a WordPress gallery. That’s why we built Envira, a drag & drop photo gallery plugin that’s both EASY, FAST and POWERFUL.
What is the vulnerability and how does it work ?
The National Vulnerability Database(NVD) describes CVE-2020–9334 as,
A stored XSS vulnerability exists in the Envira Photo Gallery plugin through 1.7.6 for WordPress. Successful exploitation of this vulnerability would allow a authenticated low-privileged user to inject arbitrary JavaScript code that is viewed by other users.
I will explain this in 4 simple steps:
- The plugin provides an authenticated user a drag & drop photo gallery feature in the control panel,
- If a malicious user were to inject some JavaScript code in “Title” field while uploading an image,
- there being no sanitization of user input, the malicious JavaScript code would be stored in the database along with the image,
- when any authenticated user would visit the plugin’s gallery, the malicious JavaScript code will be executed.
Therefore, successful exploitation of the CVE-2020-9334 may allow a remote attacker to steal potentially sensitive information, change appearance of the web page, perform phishing and drive-by-download attacks.
Proof Of Concept
Here, I am going to do a local setup of WordPress to show a Proof-Of-Concept exploitation. I will use Envira v1.6.17 to show the vulnerability since the bug has been patched in v1.7.7.
- We download, import, install, and then activate the plugin.
2. Now we go into the “Envira Gallery” tab from the sidebar and create a new gallery by clicking on the “Add New” button,
3. Give the new gallery a name and upload any image to it,
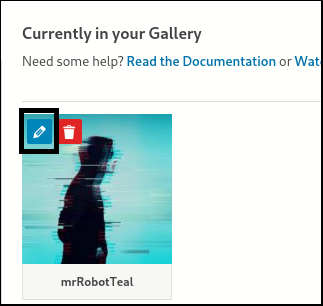
4. Now click on the pencil icon displayed on the image you just added (as shown below),
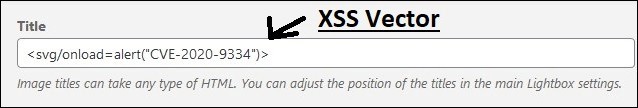
5. A dialog box should pop up. Here’s where it gets fun, Input an XSS vector in the “Title” Field,
Note:
<svg/onload=alert(“CVE-2020–9334”)>will trigger a dialog on the website. This is just for demonstration purpose to confirm that our XSS vector was infact injected. A malicious user can, in a similar way, execute any JavaScript code.
6. Now save the changes and click on “Update” button,
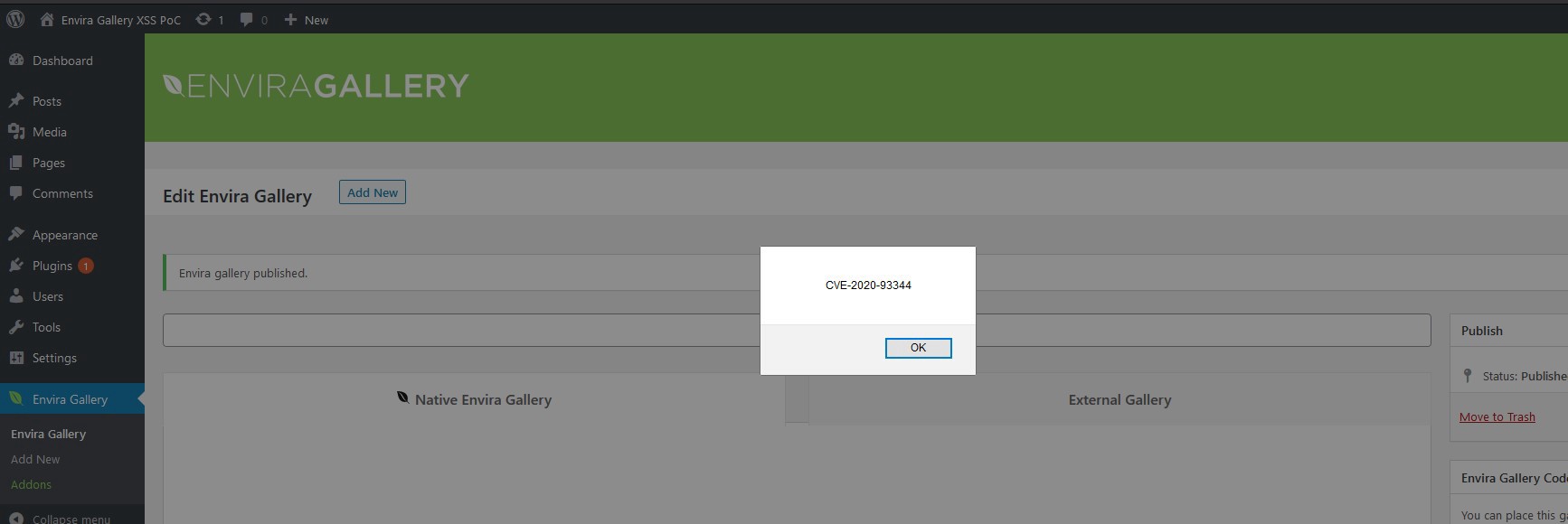
7. As soon as any other authenticated user visits the gallery page, the JavaScript code we injected would be executed.
Impact
An attacker can use XSS to send a malicious script to an unsuspecting user. In this case, an administrator. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. It can also be used to redirect the victim to a malicious site (for phishing or stealing information).
How to resolve this Envira Gallery vulnerability?
This is very simple. Navigate to your WordPress plugin section and update the plugin to the newest version — v1.7.7 (at the time of writing this blog).
We would also recommend scanning and monitoring your WordPress website with WPSec.
Vulnerabilities similar to this are found often. As such we recommend all users to keep on top of updates either by updating manually, or by activating automatic updates.
Blog post written by Eshaan Bansal.

This post and the original report on this, https://fortiguard.com/zeroday/FG-VD-20-042, don’t seem to match up with what actually is going on. They both claim the vulnerability was fixed in version 1.7.7, but there were no code changes made in that version, https://plugins.trac.wordpress.org/changeset/2245765/, and the changelog for that version is “Updated: Minor code cleanup, updating authors.” The writer of this post seems to be partially aware of that since in the post version 1.6.1.7 is used, which is over two years out of date, instead of the last version that is supposed to be vulnerable, 1.7.6.
What is showed stop working in version 1.6.5, which has a relevant changelog entry, “Fix: Escaping in the admin”. That version was released on March 21, 2019, so the timeline in the original report doesn’t match with that being related to this:
Fortinet reported the vulnerability to Envira Gallery Team on February 13, 2020
Envira Gallery Team confirmed the vulnerability on February 14, 2020
Envira Gallery Team patched the vulnerability on February 17, 2020
The same credited discoverer, Vishnupriya Ilango of Fortinet’s FortiGuard Labs, is also credited in another recent report by Fortinet that we found the version that was supposed to fix a vulnerability didn’t. In that case we were able to confirm there is a vulnerability that might be what is at issue that still exists in the plugin, https://www.pluginvulnerabilities.com/2020/03/03/bad-practices-by-fortinet-and-the-wpscan-vulnerability-database-lead-to-false-claim-of-vulnerability-being-fixed-in-wordpress-plugin/. So maybe there is an unfixed vulnerability in this plugin as well or the Fortinet is putting out reports with falsehoods, both of which would be a problem. We contacted Fortinet about the problem with the other report, but haven’t gotten any response so far.