
WordPress is a free, open-source web development platform. WordPress is a content management system (CMS) created in PHP and primarily uses MySQL or MariaDB databases. This is a more technical blog post. WordPress is today’s most user-friendly and powerful blogging, content management, e-commerce, and website builder.
A Sneak-peek on WPScan
The WPScan security scanner was developed primarily for WordPress administrators and security teams to evaluate the current state of their respective WordPress installations’ level of protection against potential threats. It checks WordPress websites for known security flaws in the application framework, plugins, themes, and other known misconfigurations. The tool was created using the Ruby programming language, and its initial version was released in 2011.
When scanning for vulnerabilities, WPScan refers to the wpvulndb.com database, which contains information about flaws in the WordPress core, plugins, and themes. To use WPScan, you do not need to access the WordPress dashboard or the source code. When scanning your site, WPScan takes the same approach hackers do, i.e., collecting data and comparing it to known flaws and exploits.
Working with WPScan
WPScan comes already preinstalled in Kali Linux and other security frameworks. However, if you are using any Linux distributions, Mac or Windows, you may refer to this guide: https://github.com/wpscanteam/wpscan
Updating WPScan
Before using WPScan, it is recommended to always update it so that it can fetch the latest checks.
To update the WPScan, run the following command:
wpscan --update
The next important part is to know how to run the tool itself, which is a very simple task. Run the following command:
wpscan [options]
To view all available scan options, run the following command:
wpscan --help
Scanning WordPress Security Vulnerabilities using WPScan
In the blog, we will discuss about exploring WPScan in depth and identifying vulnerabilities in the WordPress instance. We will be using dvwp for the practical demonstration.
To perform a simple quick scan, run the following command:
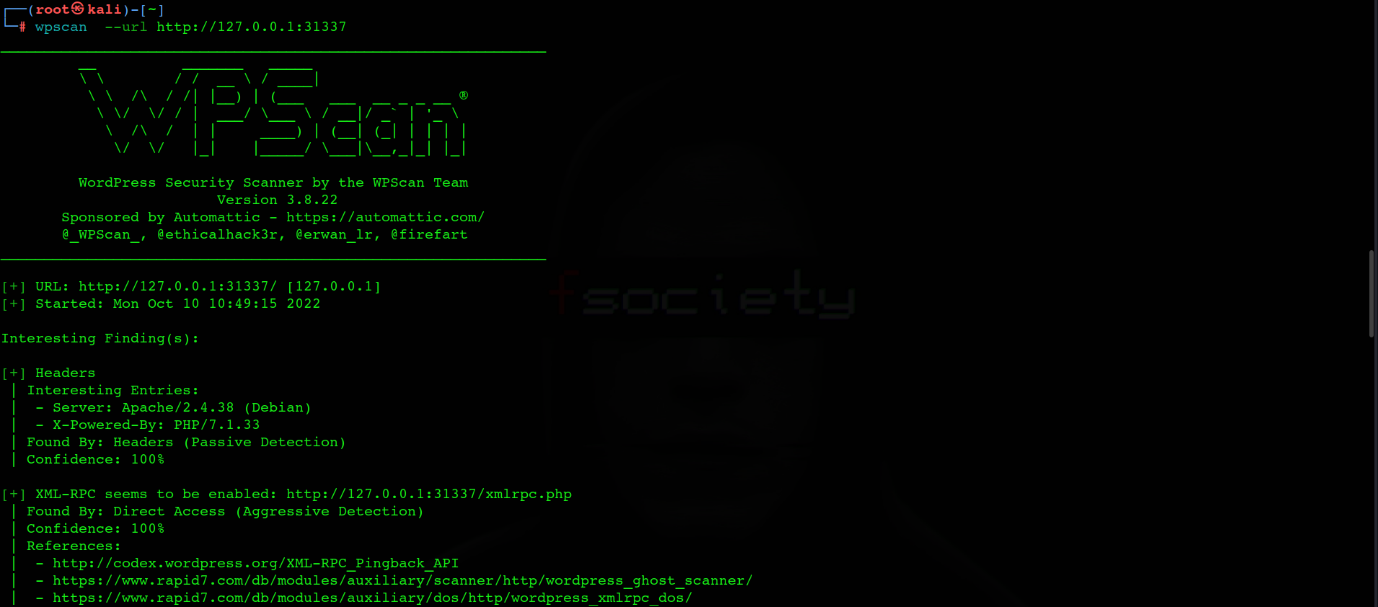
wpscan --url http://127.0.0.1:31337/
When WPScan has finished analyzing the code of your website, it will provide you with a list of interesting findings including but not limited to as shown in the screenshots below:
- WordPress version
- XMLRPC
- WordPress themes
- WordPress plugins
- Misc. basic information
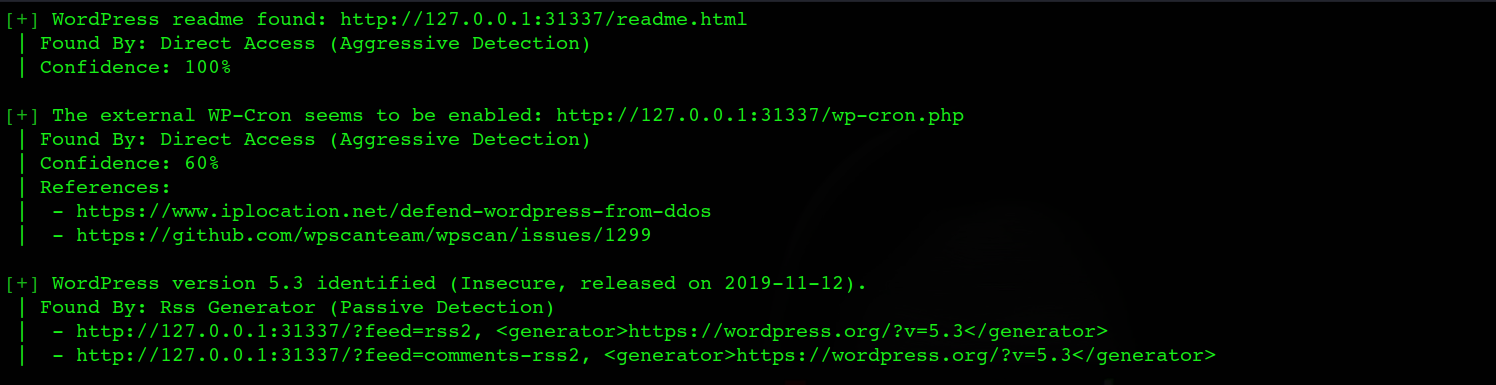
A basic scan would reveal whether a theme or plugin is using an outdated version.It will not show whether or not there are any particular vulnerabilities with that version. To obtain this information, it is required to use the WPScan Vulnerability Database API.
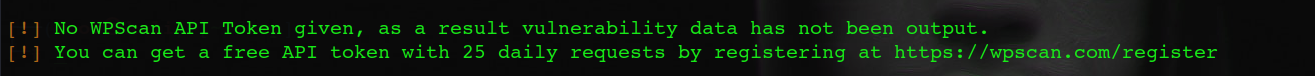
You will see a message at the bottom of your scan results. To get a free token with limited requests, you can register at https://wpscan.com/. According to WPScan, the average WordPress site has 22 plugins installed. Therefore, the 25 API queries included in the free plan should be sufficient for most uses. If you need to scan more sites every day or have additional plugins on your site, you must upgrade your subscription accordingly.
This can be done by following the below simple steps:
- Register for an account at https://wpscan.com/
- Log in and navigate to the profile section to get your API token
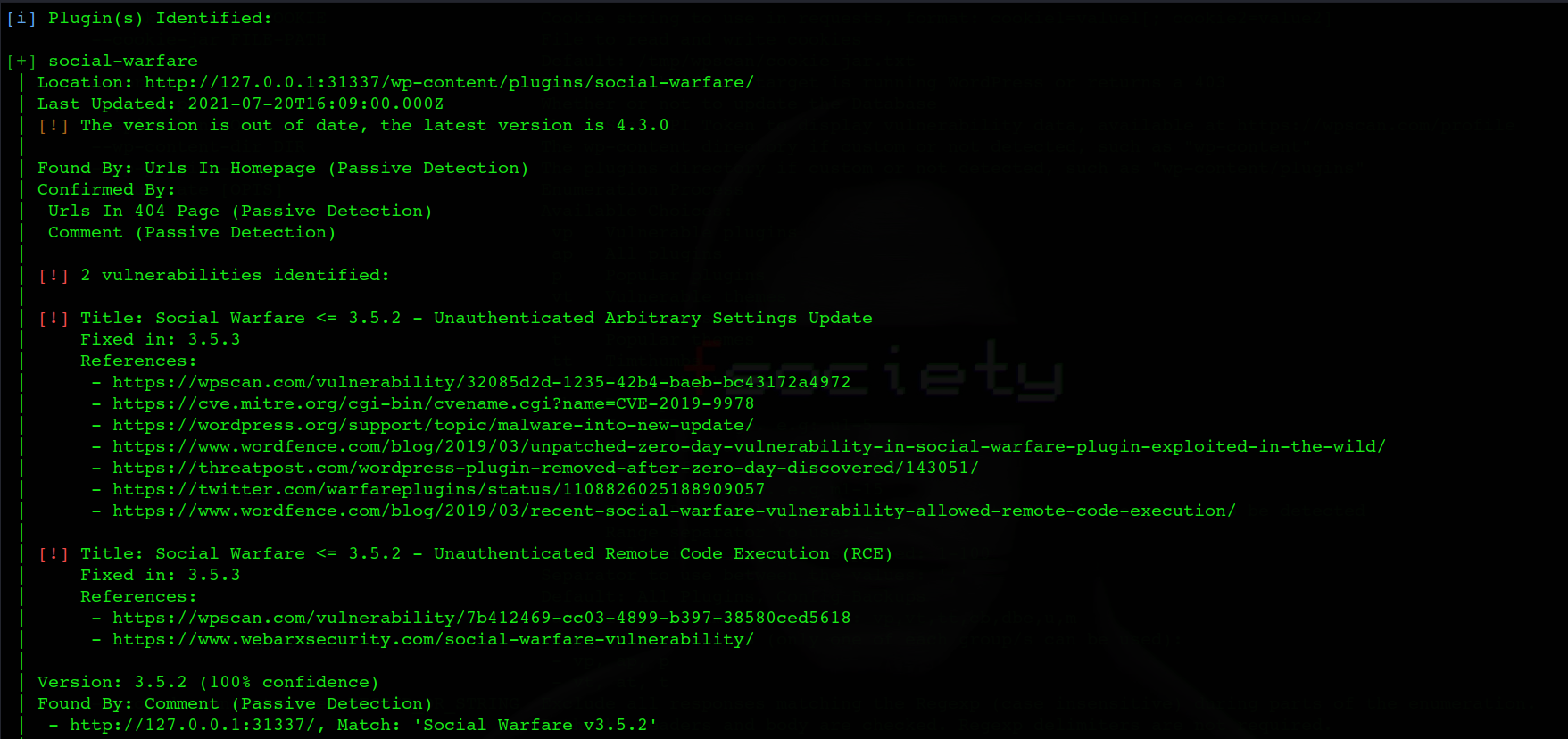
To check for the vulnerable plugins, run the following command:
wpscan -- url http://127.0.0.1:31337/ -e vp -- api-token (TOKEN)
Here, -e stands for enumeration and vp for vulnerable plugins. The scan output will look like the following:
Simply changing the vp to vt (for “vulnerable themes”) will allow you to search your website for potentially harmful themes. The command will look like the following:
wpscan -- url http://127.0.0.1:31337/ -e vt -- api-token (TOKEN)

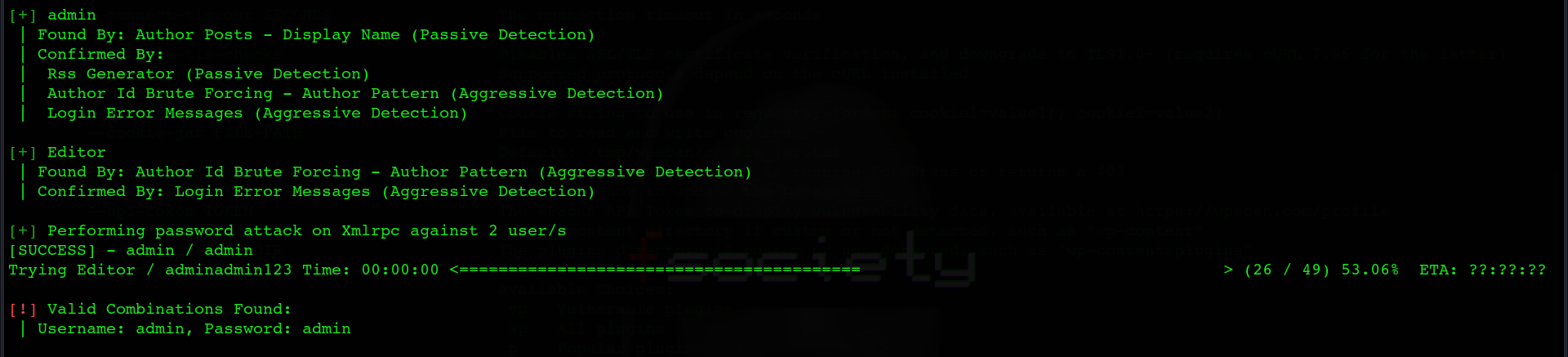
However, There is more you can do with WPScan. Another significant danger to the safety of the WordPress website is password attacks. WPScan also performs user enumeration to check which usernames are visible to outsiders.
wpscan -- url http://127.0.0.1:31337/ -e u -- api-token (TOKEN)
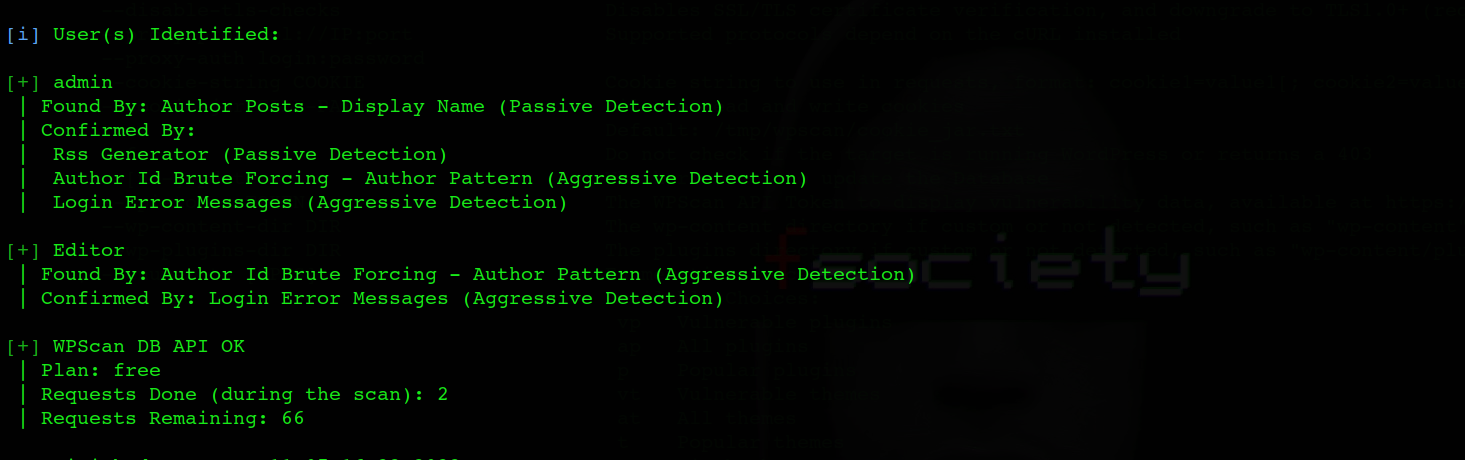
WPScan will utilize various methods to make its guesses: identifying usernames depending on publicly accessible information on your website.
Since the usernames were discovered in the last scan, to perform a brute force attack, you need to provide a password list containing all possible passwords of the WordPress website.
wpscan -- url http://127.0.0.1:31337/ --passwords path_to_password_file -- api-token (TOKEN)
You can also select the detection method while performing a scan using the following commands:
wpscan --url http://127.0.0.1:31337/ --detection-mode MODE
Available modes are: mixed, passive, and aggressive.
Mixed mode, which is the default mode, is always best during the scan as it uses both passive and aggressive methods.
WPScan also allows setting custom cookies while sending web requests during the scan.
format: cookie1=value1[; cookie2=value2]
wpscan --url http://127.0.0.1:31337/ --cookie-string COOKIE
If the target is protected behind the firewall, some options are available to avoid detection from the firewall and make less noise while scanning:
Random user agent
The below command will use a random user agent while performing the scan which is often helpful in bypassing the restrictions.
wpscan --url http://127.0.0.1:31337/ --random-user-agent
Throttle
–throttle Milliseconds
wpscan --url http://127.0.0.1:31337/ --throttle 2000
This command will wait for the provided amount of milliseconds before making another request. This helps in bypassing the rate-limiting checks and getting blocked by firewalls.
Stealthy
This is the best scan option to avoid noise and firewall detection. This scan is the alias for
–random-user-agent –detection-mode passive –plugins-version-detection passive
wpscan --url http://127.0.0.1:31337/ --stealthy
Force
Force is another good command to perform force scanning if the target returns a 403 response.
wpscan --url http://127.0.0.1:31337/ --force
WPScan also shows if the site is vulnerable to manual pentesting vulnerabilities such as SQL Injection, File upload vulnerability, Stored XSS, and Remote code execution, with the confidence level to avoid false positives.
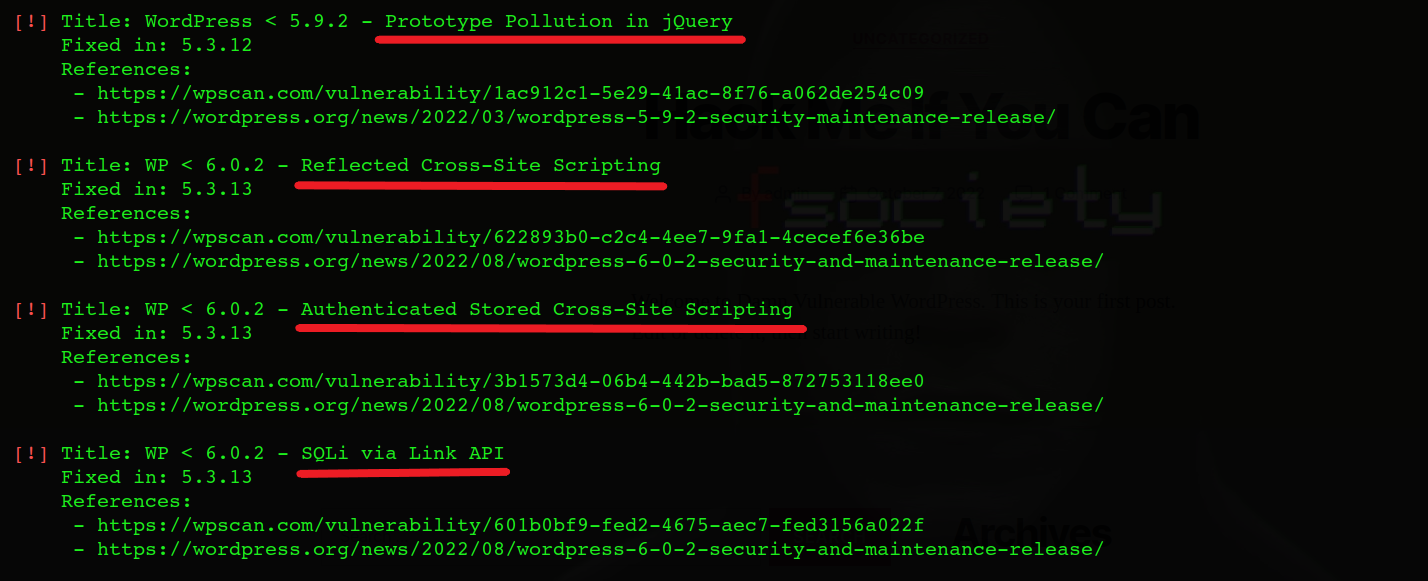
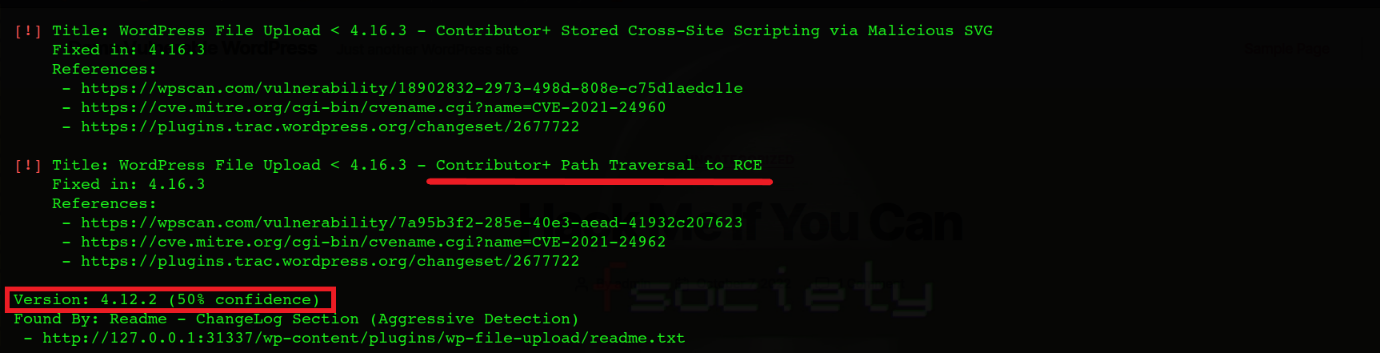
References & Further Readings
- https://www.exploit-db.com/docs/english/45556-wordpress-penetration-testing-using-wpscan-and-metasploit.pdf
- https://www.hackingtutorials.org/web-application-hacking/hack-a-wordpress-website-with-wpscan/
- https://geekflare.com/wordpress-vulnerability-scanner-wpscan/
WPScan is owned by Automattic since last year, the owners of WordPress.com and others. WPScan is also integrated into JetPack (Protect). We also recommend running WPScan using Docker, which is simple and does not require installing many third party dependencies.
